眼瞎的小伙伴玩不了MISC,嘻嘻~
001 flag
真·签到题
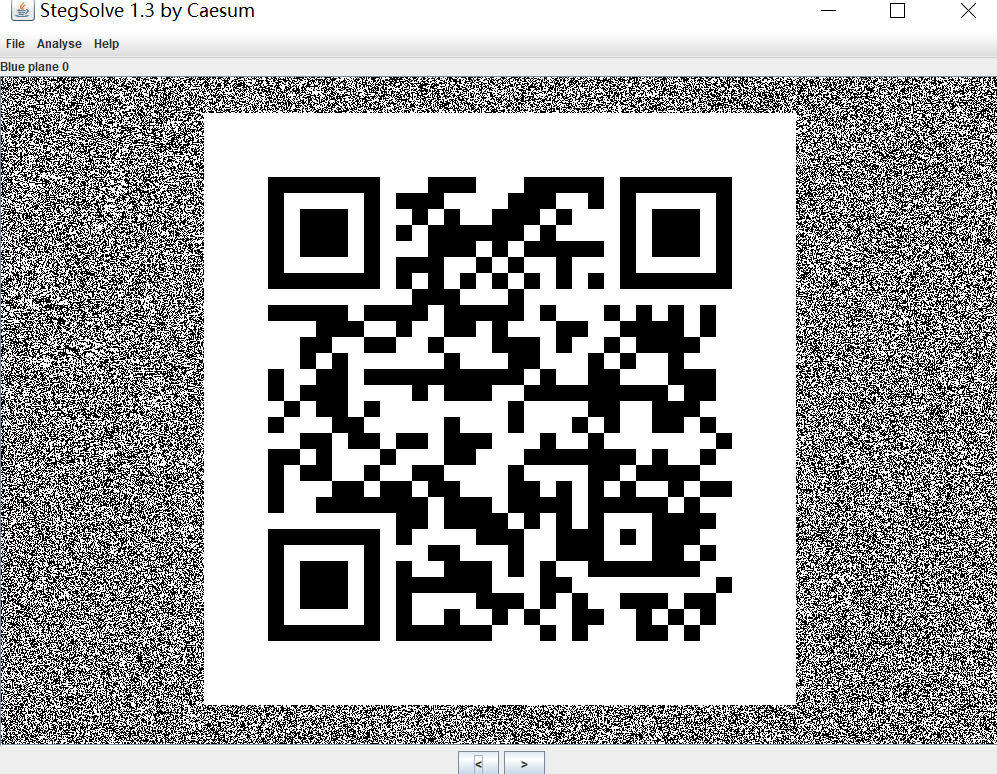
002 corgi can fly

用StegSolve打开
003 television
winhex打开,搜索FLAG即可。
我开始是搜索flag没搜到,所以暂时跳过了这题,哭唧唧
004 meow

foremost拿到一个压缩包和一张图片。压缩包里也有一张图片,且crc相同。明文攻击
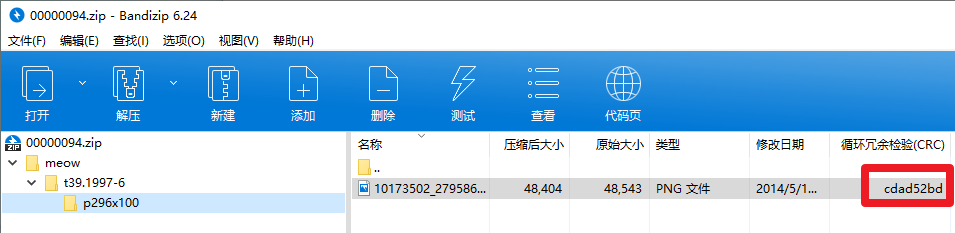
root@kali:~# cd ctf
root@kali:~/ctf# ls
meow.png
root@kali:~/ctf# foremost meow.png
Processing: meow.png
|foundat=meow/UT
foundat=meow/flagUT
*|
root@kali:~/ctf# mv ./output/png/00000000.png 00000000.png
root@kali:~/ctf# mv ./output/zip/00000094.zip 00000094.zip
root@kali:~/ctf# zip -r 00000000.zip 00000000.png
adding: 00000000.png (deflated 0%)
root@kali:~/ctf# 下面是安装pkcrack的脚本,脚本来源:记一道明文破解的漫长斗争史
#!/bin/bash -ex
wget https://www.unix-ag.uni-kl.de/~conrad/krypto/pkcrack/pkcrack-1.2.2.tar.gz
tar xzf pkcrack-1.2.2.tar.gz
cd pkcrack-1.2.2/src
make
mkdir -p ../../bin
cp extract findkey makekey pkcrack zipdecrypt ../../bin
cd ../../新建pkcrack-install.sh,将上面的脚本写入此文件,如果提示没有权限,可以chmod +x pkcrack-install.sh
然后shell终端内./pkcrack-install.sh,运行脚本。
root@kali:~/tool# ./pkcrack-install.sh
./pkcrack-install.sh: line 1: !/bin/bash: No such file or directory
--2019-10-25 22:37:33-- https://www.unix-ag.uni-kl.de/~conrad/krypto/pkcrack/pkcrack-1.2.2.tar.gz
Resolving www.unix-ag.uni-kl.de (www.unix-ag.uni-kl.de)... 131.246.124.83, 2001:638:208:ef34:0:ff:fe00:83
Connecting to www.unix-ag.uni-kl.de (www.unix-ag.uni-kl.de)|131.246.124.83|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 174208 (170K) [application/x-gzip]
Saving to: ‘pkcrack-1.2.2.tar.gz’
pkcrack-1.2.2.tar.g 100%[===================>] 170.12K 3.04KB/s in 56s
2019-10-25 22:38:31 (3.04 KB/s) - ‘pkcrack-1.2.2.tar.gz’ saved [174208/174208]
gcc -O6 -Wall -c -o crc.o crc.c
crc.c:24:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: crc.c,v 1.3 1997/09/18 18:07:24 lucifer Release1_2_1 $";
^~~~~
gcc -O6 -Wall -c -o mktmptbl.o mktmptbl.c
mktmptbl.c: In function ‘preCompTemp’:
mktmptbl.c:58:5: warning: implicit declaration of function ‘memset’ [-Wimplicit-function-declaration]
memset(numEntries, 0, sizeof(numEntries));
^~~~~~
mktmptbl.c:58:5: warning: incompatible implicit declaration of built-in function ‘memset’
mktmptbl.c:58:5: note: include ‘<string.h>’ or provide a declaration of ‘memset’
mktmptbl.c:47:1:
+#include <string.h>
mktmptbl.c:58:5:
memset(numEntries, 0, sizeof(numEntries));
^~~~~~
mktmptbl.c: In function ‘initMulTab’:
mktmptbl.c:93:5: warning: incompatible implicit declaration of built-in function ‘memset’
memset(mTab2Counter, 0, sizeof(mTab2Counter));
^~~~~~
mktmptbl.c:93:5: note: include ‘<string.h>’ or provide a declaration of ‘memset’
At top level:
mktmptbl.c:43:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: mktmptbl.c,v 1.9 2002/11/02 15:12:06 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o main.o main.c
main.c:131:6: warning: return type of ‘main’ is not ‘int’ [-Wmain]
void main( int argc, char **argv )
^~~~
main.c:70:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: main.c,v 1.15 2002/11/12 16:58:02 lucifer Exp $";
^~~~~
main.c: In function ‘main’:
main.c:265:2: warning: ‘plain’ may be used uninitialized in this function [-Wmaybe-uninitialized]
close( plain );
^~~~~~~~~~~~~~
main.c:267:2: warning: ‘crypt’ may be used uninitialized in this function [-Wmaybe-uninitialized]
close( crypt );
^~~~~~~~~~~~~~
gcc -O6 -Wall -c -o stage1.o stage1.c
stage1.c:41:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: stage1.c,v 1.8 2002/01/31 16:27:08 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o keystuff.o keystuff.c
keystuff.c:32:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: keystuff.c,v 1.5 2002/11/02 15:12:06 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o stage2.o stage2.c
stage2.c:56:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: stage2.c,v 1.16 2003/01/03 15:18:18 lucifer Exp $";
^~~~~
stage2.c: In function ‘recursion2’:
stage2.c:293:33: warning: ‘oldValue’ may be used uninitialized in this function [-Wmaybe-uninitialized]
if( !hadIt || oldValue != newKey )
~~~~~~~~~^~~~~~~~~
stage2.c: In function ‘buildKey2Lists’:
stage2.c:293:33: warning: ‘oldValue’ may be used uninitialized in this function [-Wmaybe-uninitialized]
if( !hadIt || oldValue != newKey )
~~~~~~~~~^~~~~~~~~
stage2.c:263:48: note: ‘oldValue’ was declared here
uword key2j, key2iminus1, key2iminus2, newKey, oldValue;
^~~~~~~~
stage2.c:293:33: warning: ‘oldValue’ may be used uninitialized in this function [-Wmaybe-uninitialized]
if( !hadIt || oldValue != newKey )
~~~~~~~~~^~~~~~~~~
stage2.c:263:48: note: ‘oldValue’ was declared here
uword key2j, key2iminus1, key2iminus2, newKey, oldValue;
^~~~~~~~
stage2.c:293:33: warning: ‘oldValue’ may be used uninitialized in this function [-Wmaybe-uninitialized]
if( !hadIt || oldValue != newKey )
~~~~~~~~~^~~~~~~~~
stage2.c:263:48: note: ‘oldValue’ was declared here
uword key2j, key2iminus1, key2iminus2, newKey, oldValue;
^~~~~~~~
stage2.c:293:33: warning: ‘oldValue’ may be used uninitialized in this function [-Wmaybe-uninitialized]
if( !hadIt || oldValue != newKey )
~~~~~~~~~^~~~~~~~~
stage2.c:263:48: note: ‘oldValue’ was declared here
uword key2j, key2iminus1, key2iminus2, newKey, oldValue;
^~~~~~~~
stage2.c:293:33: warning: ‘oldValue’ may be used uninitialized in this function [-Wmaybe-uninitialized]
if( !hadIt || oldValue != newKey )
~~~~~~~~~^~~~~~~~~
stage2.c:263:48: note: ‘oldValue’ was declared here
uword key2j, key2iminus1, key2iminus2, newKey, oldValue;
^~~~~~~~
stage2.c:293:33: warning: ‘oldValue’ may be used uninitialized in this function [-Wmaybe-uninitialized]
if( !hadIt || oldValue != newKey )
~~~~~~~~~^~~~~~~~~
stage2.c:263:48: note: ‘oldValue’ was declared here
uword key2j, key2iminus1, key2iminus2, newKey, oldValue;
^~~~~~~~
gcc -O6 -Wall -c -o stage3.o stage3.c
stage3.c:51:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: stage3.c,v 1.10 2002/12/30 18:27:25 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o exfunc.o exfunc.c
exfunc.c:48:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: exfunc.c,v 1.9 2003/01/05 14:40:37 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o readhead.o readhead.c
readhead.c: In function ‘read_local’:
readhead.c:318:21: warning: unused variable ‘sig’ [-Wunused-variable]
unsigned long sig;
^~~
At top level:
readhead.c:71:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: readhead.c,v 1.13 2003/01/05 14:40:37 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o writehead.o writehead.c
writehead.c: In function ‘write_sig’:
writehead.c:64:52: warning: format ‘%lx’ expects argument of type ‘long unsigned int’, but argument 3 has type ‘int’ [-Wformat=]
fprintf( stderr, "Write unknown signature: 0x%08lx\n", sigType );
~~~~^ ~~~~~~~
%08x
At top level:
writehead.c:33:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: writehead.c,v 1.4 2003/01/05 14:40:37 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o zipdecrypt.o zipdecrypt.c
zipdecrypt.c: In function ‘zipdecrypt’:
zipdecrypt.c:244:47: warning: comparison of constant ‘0’ with boolean expression is always false [-Wbool-compare]
err = (!read_ddesc(infile, 0) < 0);
^
zipdecrypt.c:244:47: warning: logical not is only applied to the left hand side of comparison [-Wlogical-not-parentheses]
zipdecrypt.c:244:24: note: add parentheses around left hand side expression to silence this warning
err = (!read_ddesc(infile, 0) < 0);
^~~~~~~~~~~~~~~~~~~~~~
( )
At top level:
zipdecrypt.c:76:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: zipdecrypt.c,v 1.16 2003/01/05 14:40:37 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o debug.o debug.c
debug.c:17:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: debug.c,v 1.2 2002/01/30 15:25:26 lucifer Exp $";
^~~~~
gcc -o pkcrack -O6 -Wall crc.o mktmptbl.o main.o stage1.o keystuff.o stage2.o stage3.o exfunc.o readhead.o writehead.o zipdecrypt.o debug.o
gcc -O6 -Wall -c -o zdmain.o zdmain.c
zdmain.c:38:6: warning: return type of ‘main’ is not ‘int’ [-Wmain]
void main( int argc, char **argv )
^~~~
zdmain.c:28:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: zdmain.c,v 1.4 2002/12/28 17:01:42 lucifer Exp $";
^~~~~
gcc -o zipdecrypt -O6 -Wall zdmain.o zipdecrypt.o crc.o keystuff.o writehead.o readhead.o
gcc -O6 -Wall -c -o findkey.o findkey.c
findkey.c:59:6: warning: return type of ‘main’ is not ‘int’ [-Wmain]
void main( int argc, char **argv )
^~~~
findkey.c:48:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: findkey.c,v 1.6 2002/11/02 15:12:06 lucifer Exp $";
^~~~~
gcc -o findkey -O6 -Wall findkey.o crc.o stage3.o keystuff.o mktmptbl.o
gcc -O6 -Wall -c -o extract.o extract.c
extract.c:93:6: warning: return type of ‘main’ is not ‘int’ [-Wmain]
void main(int argc, char *argv[])
^~~~
extract.c:76:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: extract.c,v 1.12 2002/12/28 16:09:59 lucifer Exp $";
^~~~~
gcc -o extract -O6 -Wall extract.o exfunc.o readhead.o
gcc -O6 -Wall -c -o makekey.o makekey.c
makekey.c: In function ‘usage’:
makekey.c:24:5: warning: implicit declaration of function ‘exit’ [-Wimplicit-function-declaration]
exit( 1 );
^~~~
makekey.c:24:5: warning: incompatible implicit declaration of built-in function ‘exit’
makekey.c:24:5: note: include ‘<stdlib.h>’ or provide a declaration of ‘exit’
makekey.c:18:1:
+#include <stdlib.h>
makekey.c:24:5:
exit( 1 );
^~~~
makekey.c: At top level:
makekey.c:27:6: warning: return type of ‘main’ is not ‘int’ [-Wmain]
void main( int argc, char **argv )
^~~~
makekey.c:19:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: makekey.c,v 1.1 1997/02/15 09:44:44 lucifer Release1_2_1 $";
^~~~~
gcc -o makekey -O6 -Wall makekey.o crc.o keystuff.o很多报错,但是我测试时发现并没有影响正常使用。
上面的脚本把extract findkey makekey pkcrack zipdecrypt这几个工具copy到了bin文件夹(我的脚本在/root/tool,所以在/root/tool/bin)
为了可以直接在终端中使用,而不是每次使用都去相应的文件夹,我们将/root/tool/bin(这是我的路径,请换成你的)添加进环境变量。这里我们为所有用户添加永久的环境变量。
vim /etc/profile
在文件的末尾添加一句:export PATH="$PATH:/root/tool/bin"

保存后在终端键入source /etc/profile
然后重启。不重启的话,改动仅对当前终端窗口有效。
参考:Linux环境变量总结,linux 环境变量设置(临时 + 永久)
此时,在终端内可以直接使用pkcrack。
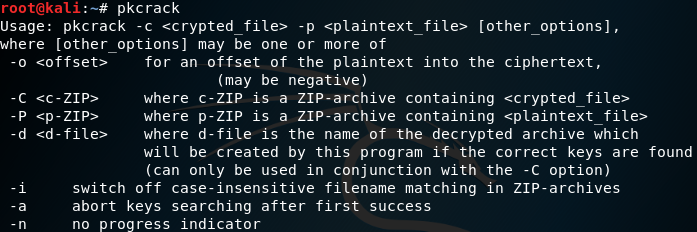
pkcrack参数(部分)
-C:要破解的目标文件(含路径)
-c:破解文件中的明文文件的名字(其路径不包括系统路径,从zip文件一层开始)
-P:压缩后的明文文件
-p:压缩的明文文件中明文文件的名字(也就是readme.txt在readme.zip中的位置)
-d:指定文件名及所在的绝对路径,将解密后的zip文件输出
root@kali:~/ctf# pkcrack -C 00000094.zip -c meow/t39.1997-6/p296x100/10173502_279586372215628_1950740854_n.png -P 00000000.zip -p 00000000.png -d flag.zip
Files read. Starting stage 1 on Fri Oct 25 23:01:00 2019
Generating 1st generation of possible key2_48403 values...done.
Found 4194304 possible key2-values.
Now we're trying to reduce these...
Lowest number: 980 values at offset 42158
Lowest number: 944 values at offset 42142
Lowest number: 911 values at offset 42114
Lowest number: 874 values at offset 42108
Lowest number: 848 values at offset 42099
Lowest number: 834 values at offset 42096
Lowest number: 833 values at offset 42095
Lowest number: 824 values at offset 42083
Lowest number: 786 values at offset 42082
Lowest number: 776 values at offset 42078
Lowest number: 721 values at offset 42073
Lowest number: 701 values at offset 42063
Lowest number: 678 values at offset 41929
Lowest number: 672 values at offset 41883
Lowest number: 663 values at offset 41882
Lowest number: 612 values at offset 41693
Lowest number: 548 values at offset 41691
Lowest number: 546 values at offset 41357
Lowest number: 521 values at offset 41347
Lowest number: 482 values at offset 41186
Lowest number: 426 values at offset 41048
Lowest number: 413 values at offset 41013
Lowest number: 390 values at offset 41012
Lowest number: 374 values at offset 41006
Lowest number: 371 values at offset 41004
Lowest number: 335 values at offset 41003
Lowest number: 311 values at offset 29709
Lowest number: 284 values at offset 29706
Lowest number: 266 values at offset 29705
Lowest number: 263 values at offset 29703
Lowest number: 260 values at offset 29702
Lowest number: 240 values at offset 29701
Lowest number: 221 values at offset 29683
Lowest number: 211 values at offset 13941
Lowest number: 206 values at offset 13934
Lowest number: 194 values at offset 13933
Lowest number: 178 values at offset 13932
Lowest number: 169 values at offset 13928
Lowest number: 166 values at offset 12839
Lowest number: 156 values at offset 12837
Lowest number: 132 values at offset 12836
Lowest number: 131 values at offset 12832
Lowest number: 114 values at offset 12830
Lowest number: 102 values at offset 12829
Lowest number: 99 values at offset 12816
Done. Left with 99 possible Values. bestOffset is 12816.
Stage 1 completed. Starting stage 2 on Fri Oct 25 23:01:17 2019
Ta-daaaaa! key0=f2a88f48, key1=bcd2cae4, key2=bd86e3f7
Probabilistic test succeeded for 35592 bytes.
Ta-daaaaa! key0=f2a88f48, key1=bcd2cae4, key2=bd86e3f7
Probabilistic test succeeded for 35592 bytes.
Ta-daaaaa! key0=f2a88f48, key1=bcd2cae4, key2=bd86e3f7
Probabilistic test succeeded for 35592 bytes.
Ta-daaaaa! key0=f2a88f48, key1=bcd2cae4, key2=bd86e3f7
Probabilistic test succeeded for 35592 bytes.
Stage 2 completed. Starting zipdecrypt on Fri Oct 25 23:01:18 2019
Decrypting meow/flag (7ca54613495f8d895211c482)... OK!
Decrypting meow/t39.1997-6/p296x100/10173502_279586372215628_1950740854_n.png (7cc69c9de15dc6a6f74f602f)... OK!
Finished on Fri Oct 25 23:01:18 2019
root@kali:~/ctf# flag.zip就是消去密码的压缩包,打开
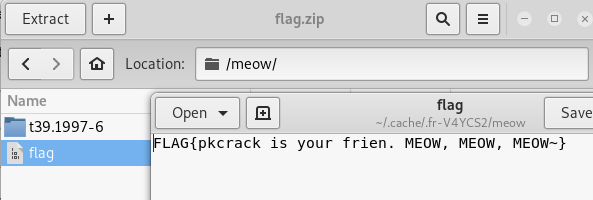
踩坑
开始时如图进行压缩
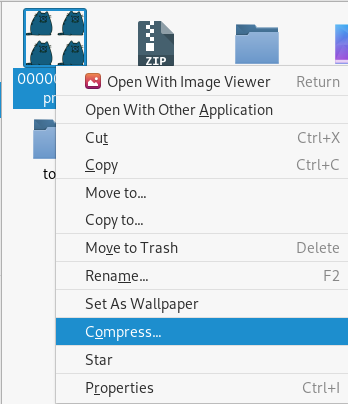
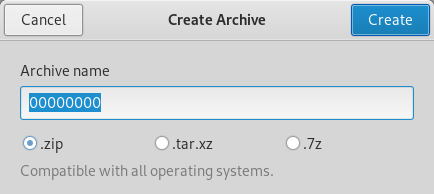
得到得压缩包中得crc也是相同的,但是使用pkcrack的时候,错误如下:
root@kali:~/ctf# pkcrack -C 00000094.zip -c meow/t39.1997-6/p296x100/10173502_279586372215628_1950740854_n.png -P 00000000.zip -p 00000000.png -d flag.zip
Error reading ZIP file: Success卡了很久,后来使用内置zip压缩命令zip -r 00000000.zip 00000000.png,这才成功明文攻击。
对比一下两种方式得到的压缩包,发现十六进制数据并不相同。所以说,不同的压缩方式(软件),即使目标压缩类型相同,得到的数据也未必相同。
别人的踩坑记录:记一道明文破解的漫长斗争史
005 where is flag
打开后发现是海量的flag字符串的变形。题目描述中提示正则表达式
import re
with open('flag')as f:
t = f.read()
flag = re.findall(r'FLAG{[a-zA-Z0-9 ]+?}', t)
for i in flag:
print(i)FLAG{VizQLeu9M3aybJBA3f1AgFROGyuTLXZ2oeRbKf1Agf1AgFLAG9hBTI}
开始时规则设置为r'FLAG{.+?}',提取出很多flag,所以加强了规则
008 pusheen.txt
很容易猜测两个图像分别代表0和1
import re
with open('pusheen.txt','r',encoding='utf-8')as f:
s = f.read()
a = ''' ▐▀▄ ▄▀▌ ▄▄▄▄▄▄▄
▌ ▀▄▄▄▄▄▀ ▐▄▀▀ ██ ██ ▀▀▄
▐ ▀ ▀ ▀ ▀▄
▌ ▄ ▀▄
▀█ █▌ █ ▐█ ▀ ▌
▀▌ ▀ ▀ ▀▀ ▐ ▄▄
▐ ▌▄█ █
▐ █ █▀
▐ █▀
▐ ▌
▌ ▐
▐ ▌
▌ ▐
▐▄ ▄▌
▀▄▄▀▀▀▀▀▄▄▀▀▀▀▀▀▀▄▄▀▀▀▀▀▄▄▀
'''
b = ''' ▐▀▄ ▄▀▌ ▄▄▄▄▄▄▄
▌▒▒▀▄▄▄▄▄▀▒▒▐▄▀▀▒██▒██▒▀▀▄
▐▒▒▒▒▀▒▀▒▀▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▀▄
▌▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▄▒▒▒▒▒▒▒▒▒▒▒▒▀▄
▀█▒▒▒█▌▒▒█▒▒▐█▒▒▒▀▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▌
▀▌▒▒▒▒▒▒▀▒▀▒▒▒▒▒▒▀▀▒▒▒▒▒▒▒▒▒▒▒▒▒▒▐ ▄▄
▐▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▌▄█▒█
▐▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒█▒█▀
▐▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒█▀
▐▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▌
▌▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▐
▐▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▌
▌▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▐
▐▄▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▄▌
▀▄▄▀▀▀▀▀▄▄▀▀▀▀▀▀▀▄▄▀▀▀▀▀▄▄▀
'''
s = s.replace(a,'0').replace(b,'1').replace('\n','')
print(s)输出为010001100100110001000001010001110111101101010000011101010111001101101000011001010110010101101110001000000100111101001001010011110100111101001111010010010100100101001111010011110100100101001111010011110100100101001001010011110100111101001111010010010100111101001111010011110100111101001111010010010100111101001001010011110100111101001111010010010100100101001001001000000100001101110101011101000110010101111101
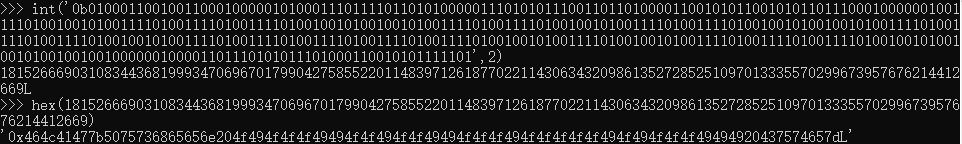
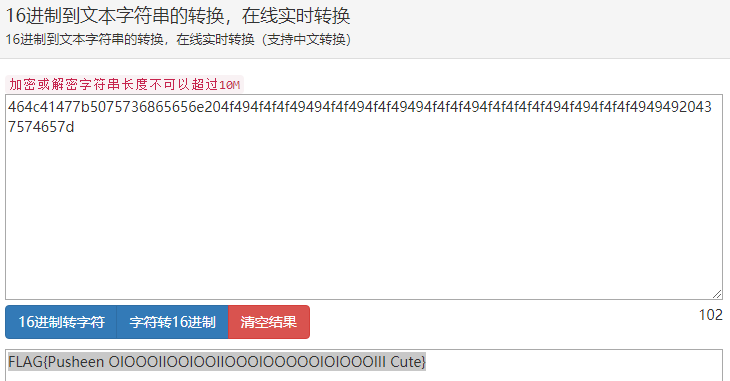
转换成十六进制,再转换成字符串
099 easy pdf
kali下使用pdftohtml将pdf文件转换为html,隐藏在pdf文件中的flag就在html中显示出来了
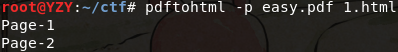
不指定html的名字则默认pdf的文件名

100 this is a pen
方法同上
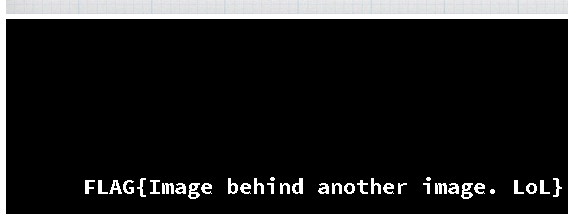
FLAG{Image behind another image. LoL}