逆向题解稍后发,先把密码学的放上来。
全场两解的rsa,赛后也没搜到题解,只能作罢。哎,真想知道这两个师傅是怎么做的。
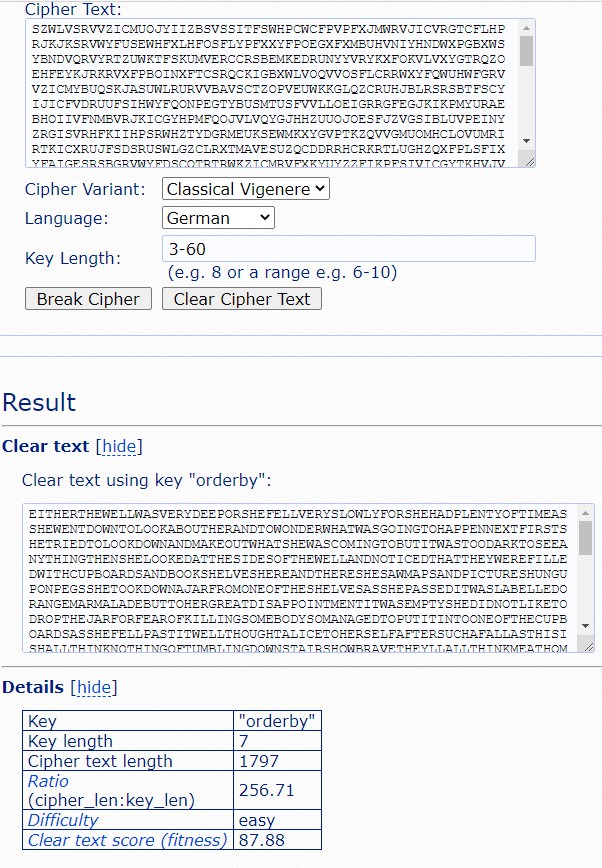
维吉尼亚
水题,直接上https://www.guballa.de/vigenere-solver
LFSRXOR
线性反馈生成密钥流,与明文进行循环异或。
给出两个密钥分别与明文异或后的密文。
两个密文异或得到两个密钥的异或结果。
两个线性反馈的抽头是确定的,后面的随机打乱密钥流顺序的操作,从增强算法强度的角度来说,其实是无效的,随机的初始状态也是无效的。最终可以把密钥流的取值限定在一个特定的集合。
fpoly=[4,3]的所有可能的密钥流是:
[0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
[19, 94, 38, 188, 77, 120, 154, 241, 53, 226, 107, 196, 215, 137, 175]
[154, 241, 53, 226, 107, 196, 215, 137, 175, 19, 94, 38, 188, 77, 120]
[137, 175, 19, 94, 38, 188, 77, 120, 154, 241, 53, 226, 107, 196, 215]
[77, 120, 154, 241, 53, 226, 107, 196, 215, 137, 175, 19, 94, 38, 188]
[94, 38, 188, 77, 120, 154, 241, 53, 226, 107, 196, 215, 137, 175, 19]
[215, 137, 175, 19, 94, 38, 188, 77, 120, 154, 241, 53, 226, 107, 196]
[196, 215, 137, 175, 19, 94, 38, 188, 77, 120, 154, 241, 53, 226, 107]
[38, 188, 77, 120, 154, 241, 53, 226, 107, 196, 215, 137, 175, 19, 94]
[53, 226, 107, 196, 215, 137, 175, 19, 94, 38, 188, 77, 120, 154, 241]
[188, 77, 120, 154, 241, 53, 226, 107, 196, 215, 137, 175, 19, 94, 38]
[175, 19, 94, 38, 188, 77, 120, 154, 241, 53, 226, 107, 196, 215, 137]
[107, 196, 215, 137, 175, 19, 94, 38, 188, 77, 120, 154, 241, 53, 226]
[120, 154, 241, 53, 226, 107, 196, 215, 137, 175, 19, 94, 38, 188, 77]
[241, 53, 226, 107, 196, 215, 137, 175, 19, 94, 38, 188, 77, 120, 154]
[226, 107, 196, 215, 137, 175, 19, 94, 38, 188, 77, 120, 154, 241, 53]其中0000这个初始状态对于的全0的密钥流,是无效的。除此之外,共2的n次方-1个不同的密钥流。
取集合你会发现,其实数据是相同的,只是排序顺序问题。
fpoly=[5,4,2,1]的所有可能的状态是:
[106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251, 56]
[190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72]
[13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103]
[206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190]
[53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156]
[179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47]
[179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47]
[112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246]
[190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72]
[26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206]
[169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225]
[145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26]
[56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251]
[217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23]
[156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125]
[34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53]
[53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156]
[47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82]
[145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26]
[34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53]
[195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217]
[145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26]
[225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236]
[95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164]
[56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251]
[251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34]
[47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82]
[217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23]
[125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206, 26, 145]
[190, 206, 26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72]
[26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206]
[26, 145, 125, 156, 53, 34, 251, 56, 106, 69, 246, 112, 212, 139, 236, 225, 169, 23, 217, 195, 82, 47, 179, 134, 164, 95, 103, 13, 72, 190, 206]以上的两组数据可以用下面的脚本测出:
from pylfsr import LFSR
from Crypto.Util.number import *
def f(s):
str_list = list(s)
print(str_list)
#sl = set(str_list)
#print(sl)
for i1 in range(2):
for i2 in range(2):
for i3 in range(2):
for i4 in range(2):
L4 = LFSR(fpoly=[4,3],initstate =[i1,i2,i3,i4],verbose=False)
data = L4.runFullCycle()
k4 = b""
for _ in range(len(data)):
a = b''
for _ in range(8):
a += str(L4.next()).encode()
k4 += long_to_bytes(int(a,2))
f(k4)
print('\n\n\n\n')
for i1 in range(2):
for i2 in range(2):
for i3 in range(2):
for i4 in range(2):
for i5 in range(2):
L5 = LFSR(fpoly=[5,4,2,1],initstate ='random',verbose=False)
data = L5.runFullCycle()
k5 = b""
for _ in range(len(data)):
a = b''
for _ in range(8):
a += str(L5.next()).encode()
k5 += long_to_bytes(int(a,2))
f(k5)前面我们说过,可以拿到k4和k5的异或结果,然后走一波z3就可以了。注意异或问题很容易多解,所以我们要限定取值。本来需要k4,k5同时限定,但是我限定完k4就已经可以跑出flag了。
import struct
from z3 import *
enc1 = b'\xbb\xd3\x08\x15\xc6:\x08\xb2\xb2\x9f\xe4p\xc7\xec\x7f\xfd)\xf6f\x9c\xe4\xd12\xaeJ\x81\xb1\x88\xab\xa5V\xa9\x88\x14\xdf`~\xf6\xdbJ\xb4\x06S!0\xbb\xe4\x1a\xe6R\x8e\x84X\x19K\x95\x07C\xe8\xb2\'\xa9\x80\x15\xec\x8f\x8dY\nK\x85\x99\xb7!\x134\xa9\xb6\x15\xcf&\r\x9b\xe1\x99\xe4]3h~\xf0\xa9\xa5\x14\xee}\xd19l\x14h\x07v *a0\x12\x14\xfe\x0f\x05\xdem\x1d\xe4s2J\x7f\xc28\xf6RR\x8e\xba\xb2m\x18M\xf1\xef!4\x17\xa8\xb4\x14\xc2\x8f\xb9Y:K\xaa\x06T!\x1b\xbb\xfd\xf6Gv\x8e\x9a\xeb\xd9K\xbb\x06N\x9a\x82c\xa9\xa0\x14\xed!\x04\xdbm\x13\xe5w3B\x7f\xd0\xa9\xbf\xb7\x9c\xe3\xd00\x83K\x86\xab3\x7f\xc1\xbb\xfd\x11\x15\xdf\x8e\x80Y\x07\xd8\xe5]2m\xe9\xbb\xce`\x91o\x8f\x8cY!\x81\xe4J\x92\x8c\xa7T\x16E\x15\xf1WMY(\xb8[\x8e2y~\xcbM\x10\x15\xc7\x1fWY\x0cK\x87\xce\xe5 !b\xa8\x83\x14\xec6\xd1!\xc8\x905\xe52L\xf1\xba\xcf\n\x9d\x9d\xe7u\xadm\x06\xe4n2r\xd8\xba\xed\xf6\x7f\x9d\xd8\xd02m\x12G\x07Y\x89\x7f\xc0\xa8\xa4\x15\xe5\x043Y\x1eJ\xae\x07n\x94\x87\xbb\xcf_\x8d\x9d\xd1\x14Y,\x9e\xe5b\xd7\x8c\x7f\xf7\xa8\x8f\x14\xc7\x8f\xb3\xb6\xf1\x93\xe4O\xdd\xc4\xdb\xba\xf6!\x15\xfd.\xd1\x18\xcf\xf6\x03\xea2E\x7f\xe1\xa9\xa5\xfe\x9d\xc9\xd1;\xd9\xee\x05\x06z\xc8\xb2\xbb\xe2\xf7{JW4\xcdm\x1a\xe5U\x8d \x0f&\x14\x7f\xf6\x9d\xd4E\xbf\xc3\xdb\xe4L\xe1\xf7\x90\xbb\xdaZ\xf4\x9d\xd13\xb8m3\xe2D3o~\xf8H\xf6U*\x07lY\x03K\xab\x07~\xa3\x87\xbb\xc9\xf7sAQ\x08Y6J\x86\x07Y\xec\xf7\xbb\xc6s\x15\xc6\x7fEY\x02J\x95\x07Z \x11\xbb\xc6T\x15\xfc-\xd0\x06\xe6\x9f-\x07^ \x15\xbb\xccz\x14\xf3\x8f\x97\xd4l9t\x85\xe8\x8a\xbe\xbb\xf9\xf6f\x9d\xf2\xd19\xa2K\xb6\xcd\xcf\xf6~\xd5\xa9\xaa\x15\xd8\x8e\xb3\x81m9\xe4f\xb2!\x1e\xba\xd8s\xfd\x11\x08W\xa1l;\x01\x07_!\x11\xbb\xdd\xf6x\x9d\xf0\x17Y\x15\xfe\x02\xc7\xa0!.W\xa9\xa5\x8f\x9c\xe8\xd1\x12m\x04\xe5s3Q~\xdd\xa9\xa3\x15\xdb\x8f\xac\xaf\xec\xbb\x10\xde2_\xba\xba\xe8\xf6f.\x1e\xd1\x17l\x06\xe4U\xdd\xf0\xd6~\x0fA\x14\xcb\x8e\xb0Y\x1fJ\xb2\xe4\xb3!"\xba\xfeU\x14\xedY\xd0>l-~\x06P 1\xbb\xf2\xf6waD\xd1(m\x12`\x06@\xb6~\xfa\xa9\xb1\xb0\x9d\xfb\x18\xfbm&\xe4v2w\xce\xba\xcbo\xd5\x07\x11QX<J\xbd\xb22O\x7f\xd8x>\xc8\x9c\xd3\xd03\x9d\xb5\x1e\xd72S\xf2ry\xf1W\x9c\xc89Y\rK\x8f\xff\x8a\xe0\xb5{\xa9\xae\xb1\x9d\xdd\xd1=\xbeK\xa3\x06e!\x08\xba\xd2\xf6j\x9c\xf6\xd0\x0fl#\xe5o\xf5\xaa~\xc2\xa9\x99\x15\xea6\xd1:\xe7\xa8\xe4n\xbb \nV\xa9\x91\x14\xf9}\xd0!m/\xe5|2o\x81\xba\xf8\r\x14\xeb\tR\xc9\xec\xdd`\xbf\xc6\x81\xdfKXW\xb3o.%\xa9\xcd\xb9\x14\xfd\x97\x83\x8eO\n\x03\xb6iuu\xab\x9d\xbc\x15\xf4\xc3\xd6\xc1'
enc2 = b'p\xfd\x1ff\xcaB\xa5\xe6`\x87\xa8\x8ci\x855\x92O8P\xa5}^\xd8\xed\x1a\x88=c\xe0\x9f\xedq\xf8\xe1%\x7fX\xd2\xba\xbe\x03\xa8\x9a\x9c\x075\x98"\xca\xed\xa4C^\xc6.j\xec\xfa\x10\xa7\xd9\x01\x06\x87\x90f\xcc\xf6\x1b\x0c\xde\xcc,\xfb\xf0\xc74\x94\xcfj\x8ay\xd5\xd2`.@\xed\xc2\xd8!DSp\xf5\x12f\xf1\xf6#\x80\xbe\x16\xa8\xaeF\xd0\xd1\xd4\xad\xb9\xf7#\x16\x08\xb2[\x1a\x87\x8b\xa0\xfaEF\xbf\x86\x8b\x8c\x90\xa4\xd5\xfbcR\xe2W\x9c\n5\x8b\xcfQ"\xf2\x16\x10\xb2I\x1a\x88\x8b\x8cj\x16\xebp\xccS\xd2\x90\xa8|q\x05\xafq\xfa\xcaHE{\x1a\xba#\xfd\x17/\xb2L\x1a\x87\x8a\x90\xc9Dmp\xef\x0ef\xf2Z|S\x00R\xfc\x1c\x9d\n5\x84\xceS\xb0\xa4M_\xff\xb9\x1a\x8a\x1d\\\x98D\\p\xcb*f\xdcV\xd0\xd5Q\xec\x1a\xfa\xf0\x91\xa8\xd4\x8a\xca\x9c-\x17\x07\xb2_\xff\n\x8a\x83\xfb\xc2\x00\x10\x87\x83\xaeF\xf7#\xd4\xbe\'\xa9\x8a$IMp\x14\xe8\xc0\xa4z\xd1\xb2H\xe6e\x8b\xb0\xcf\xb1\x01<\x87\x88g\xc2Q|H\xbe9\xa9\xad\x9c#4\x8cl8I\x0c\x17$\xb3}\x1b\x94\x01:j7\x00;\x86\xbd\xd2i\xf6\x1a\xa4\'R\xf6?\x9c\x08\xe1\xd4\xab\xdd\x8f\xa4[_\xca/@\xed\xe86\xf7\x9c\x018i\x04\xc3\x90\xa8\xaa\x0c\xde\xf2\xa8\xba?\xf4\xd39\xce\\"\xfe\x16\x0cY/]\xed\xe9l\xce\xa5\x018o,g\xdb\xf7\x12\xdag\xb6=\xfa\xccHgk\xcfH\xbf\x18\x9e\xbd\xb3u\x8f\n$Hk\x0e\xd3\xa6i\xe1\x15=\x16}R]\xb3\xa8\x82\x9b\x0b4\x9a\xcf{\xc2\xa4V\xe8:\x93\x1a\x83\x8a\x97j\t\x82\x88\x86\x80f\xf6*\xa2\xd5\xbe\x08\xa9\x98\x9c#\xf8\\\xceV\xa7\xa5L\xae&/t\xec\xfb\xd9\x02Dnp\xe8Cf\xf0U}R4\x87a\xfb\xf0I_\xd4\xaa\xb4"\xca\x16\x18>/i}\t\x03\xc1\x84\x00!\x86\x93g\xed\xf7\x1d\xc3\xbf\x01c\x06KI[\xd5\x929g\xa4t\x87\xb2\\\x1b\x8d\x0b\xd9\x0bDp\xf5om\xe1\x16\x0e}|ZR\xc4\xfb\xf2H@\xd4\xa28\\c\x17&\x07\xc8\xda~\x8b\x88\x86DS\xeb\x87\x87f\xda\xf73\r\xcaS\xd9\xfa\xfaI`\xd5\x889^R\x97\xaeF\xf6\x1a\x92N\xd8*Er\xc3\x16\xe0)\x91\xba|_Q\x83\x00>;\xff5\x82\xceX"\xd7\x17\x08P\xae\x1a\xb1\x8a\x8f\xc9Ep\xa7\x86\x86g\xf6m|o\xbf\x1c\xa9\xa1\x9c+\xc9\x1e\xcfI#\xfc\x92^\xc1\xb8\x1b\xad\x8a\x9e\xceEu\xb8$\xe0\x0b\x90\x87}[\x0fS\xcab]\xd2\xaaU\xcfh"\xfc\xa2_\xdd/y<C\x05k\x18\x00\x1aw\x1e\x9cA\xf6\x0f\x80w\x83\xae\xb8\x9d\x0e\xdc\xd4\xaf9H\\\xaf\x9ey\xef\x1b\xb4.\xd99Dd\xa2\x87\xa7f\xc6\xf6\n\x0c\xc4R\xd7\xfa\xe4Hc\xd4\xa78Jc\x9c^\xca.u\xed\xfcak&\x8b\x92\x87\x88\xee\x90\x83\x90\x0c\xd9R\xcd\x08\x9c04\xb1\xceC"\xea\xe9^\xe3\xd4\x1a\x9a\x0c[\xfa\xc5\x97\xf5>\x15\xc71\x06\x8d\xac\x19\xa0\t\x0el\xe9\xc6%4\x9d\x80U\xe3\xfdF\x8d\xee\x17.+\x9b\xb3\xf0\x83w\x16\xd9'
xor = b''
for i in range(len(enc1)):
tmp = enc1[i] ^ enc2[i]
xor += struct.pack('B', tmp)
#print(xor)
#print(len(xor))
s = Solver()
k1, k2 = [], []
for i in range(0, 15):
k1.append(BitVec('k1_'+str(i), 8))
s.add(Or(Or(Or(Or(Or(Or(Or(Or(Or(Or(Or(Or(Or(Or(k1[i] == 226, k1[i] == 196), k1[i] == 38), k1[i] == 137), k1[i] == 107), k1[i] == 77), k1[i] == 175), k1[i] == 241), k1[i] == 19), k1[i] == 53), k1[i] == 215), k1[i] == 120), k1[i] == 154), k1[i] == 188), k1[i] == 94))
for i in range(0, 31):
k2.append(BitVec('k2_'+str(i), 8))
# {226, 196, 38, 137, 107, 77, 175, 241, 19, 53, 215, 120, 154, 188, 94}
for i in range(len(enc1)):
i1 = i % 15
i2 = i % 31
print(k1[i1],'^', k2[i2], '==', xor[i])
s.add(k1[i1] ^ k2[i2] == xor[i])
print(s.check())
#print(s.model())
key1 = []
for i,name in enumerate(k1):
key1.append(s.model()[name].as_long())
print('key1:', key1)
key2 = []
for i,name in enumerate(k2):
#print(name)
key2.append(s.model()[name].as_long())
print('key2:', key2)
flag1 = b''
for i in range(len(enc1)):
tmp = enc1[i] ^ key1[i % 15]
flag1 += struct.pack('B', tmp)
flag2 = b''
for i in range(len(enc2)):
tmp = enc2[i] ^ key2[i % 31]
flag2 += struct.pack('B', tmp)
print(flag1 == flag2)
print(flag2)z3那个约束我没找到相关的函数,只能手动写Or。太麻烦了,所以简单写了个小递归:
moban = '''Or(%s, %s)'''
key = [226, 196, 38, 137, 107, 77, 175, 241, 19, 53, 215, 120, 154, 188, 94]
def f(index, last):
#print(index)
#print(last)
if index == 14:
print(last)
return
f(index+1, moban % (last, 'k1[i] == %d' % key[index+1]))
f(0, 'k1[i] == %d' % key[0])赛后看了看师傅的wp,他用的攻击方式应该是选择明文(我也不太清楚这个是选择明文攻击还是已知明文攻击,应该是选择明文吧)攻击。好家伙,直接绕过了整个lfsr。属实牛逼。果然我还是菜啊。。。
这里放下他的脚本:
# 商业转载请联系作者获得授权,非商业转载请注明出处。
# For commercial use, please contact the author for authorization. For non-commercial use, please indicate the source.
# 协议(License):署名-非商业性使用-相同方式共享 4.0 国际 (CC BY-NC-SA 4.0)
# 作者(Author):Snowywar
# 链接(URL):http://snowywar.top/wordpress/index.php/2020/11/02/hxbwriteup/
# 来源(Source):魔法少女雪殇
from pylfsr import LFSR
from Crypto.Util.number import *
import random,string
dirct = string.ascii_letters+string.digits+"{}"
enc1 = b'\xbb\xd3\x08\x15\xc6:\x08\xb2\xb2\x9f\xe4p\xc7\xec\x7f\xfd)\xf6f\x9c\xe4\xd12\xaeJ\x81\xb1\x88\xab\xa5V\xa9\x88\x14\xdf`~\xf6\xdbJ\xb4\x06S!0\xbb\xe4\x1a\xe6R\x8e\x84X\x19K\x95\x07C\xe8\xb2\'\xa9\x80\x15\xec\x8f\x8dY\nK\x85\x99\xb7!\x134\xa9\xb6\x15\xcf&\r\x9b\xe1\x99\xe4]3h~\xf0\xa9\xa5\x14\xee}\xd19l\x14h\x07v *a0\x12\x14\xfe\x0f\x05\xdem\x1d\xe4s2J\x7f\xc28\xf6RR\x8e\xba\xb2m\x18M\xf1\xef!4\x17\xa8\xb4\x14\xc2\x8f\xb9Y:K\xaa\x06T!\x1b\xbb\xfd\xf6Gv\x8e\x9a\xeb\xd9K\xbb\x06N\x9a\x82c\xa9\xa0\x14\xed!\x04\xdbm\x13\xe5w3B\x7f\xd0\xa9\xbf\xb7\x9c\xe3\xd00\x83K\x86\xab3\x7f\xc1\xbb\xfd\x11\x15\xdf\x8e\x80Y\x07\xd8\xe5]2m\xe9\xbb\xce`\x91o\x8f\x8cY!\x81\xe4J\x92\x8c\xa7T\x16E\x15\xf1WMY(\xb8[\x8e2y~\xcbM\x10\x15\xc7\x1fWY\x0cK\x87\xce\xe5 !b\xa8\x83\x14\xec6\xd1!\xc8\x905\xe52L\xf1\xba\xcf\n\x9d\x9d\xe7u\xadm\x06\xe4n2r\xd8\xba\xed\xf6\x7f\x9d\xd8\xd02m\x12G\x07Y\x89\x7f\xc0\xa8\xa4\x15\xe5\x043Y\x1eJ\xae\x07n\x94\x87\xbb\xcf_\x8d\x9d\xd1\x14Y,\x9e\xe5b\xd7\x8c\x7f\xf7\xa8\x8f\x14\xc7\x8f\xb3\xb6\xf1\x93\xe4O\xdd\xc4\xdb\xba\xf6!\x15\xfd.\xd1\x18\xcf\xf6\x03\xea2E\x7f\xe1\xa9\xa5\xfe\x9d\xc9\xd1;\xd9\xee\x05\x06z\xc8\xb2\xbb\xe2\xf7{JW4\xcdm\x1a\xe5U\x8d \x0f&\x14\x7f\xf6\x9d\xd4E\xbf\xc3\xdb\xe4L\xe1\xf7\x90\xbb\xdaZ\xf4\x9d\xd13\xb8m3\xe2D3o~\xf8H\xf6U*\x07lY\x03K\xab\x07~\xa3\x87\xbb\xc9\xf7sAQ\x08Y6J\x86\x07Y\xec\xf7\xbb\xc6s\x15\xc6\x7fEY\x02J\x95\x07Z \x11\xbb\xc6T\x15\xfc-\xd0\x06\xe6\x9f-\x07^ \x15\xbb\xccz\x14\xf3\x8f\x97\xd4l9t\x85\xe8\x8a\xbe\xbb\xf9\xf6f\x9d\xf2\xd19\xa2K\xb6\xcd\xcf\xf6~\xd5\xa9\xaa\x15\xd8\x8e\xb3\x81m9\xe4f\xb2!\x1e\xba\xd8s\xfd\x11\x08W\xa1l;\x01\x07_!\x11\xbb\xdd\xf6x\x9d\xf0\x17Y\x15\xfe\x02\xc7\xa0!.W\xa9\xa5\x8f\x9c\xe8\xd1\x12m\x04\xe5s3Q~\xdd\xa9\xa3\x15\xdb\x8f\xac\xaf\xec\xbb\x10\xde2_\xba\xba\xe8\xf6f.\x1e\xd1\x17l\x06\xe4U\xdd\xf0\xd6~\x0fA\x14\xcb\x8e\xb0Y\x1fJ\xb2\xe4\xb3!"\xba\xfeU\x14\xedY\xd0>l-~\x06P 1\xbb\xf2\xf6waD\xd1(m\x12`\x06@\xb6~\xfa\xa9\xb1\xb0\x9d\xfb\x18\xfbm&\xe4v2w\xce\xba\xcbo\xd5\x07\x11QX<J\xbd\xb22O\x7f\xd8x>\xc8\x9c\xd3\xd03\x9d\xb5\x1e\xd72S\xf2ry\xf1W\x9c\xc89Y\rK\x8f\xff\x8a\xe0\xb5{\xa9\xae\xb1\x9d\xdd\xd1=\xbeK\xa3\x06e!\x08\xba\xd2\xf6j\x9c\xf6\xd0\x0fl#\xe5o\xf5\xaa~\xc2\xa9\x99\x15\xea6\xd1:\xe7\xa8\xe4n\xbb \nV\xa9\x91\x14\xf9}\xd0!m/\xe5|2o\x81\xba\xf8\r\x14\xeb\tR\xc9\xec\xdd`\xbf\xc6\x81\xdfKXW\xb3o.%\xa9\xcd\xb9\x14\xfd\x97\x83\x8eO\n\x03\xb6iuu\xab\x9d\xbc\x15\xf4\xc3\xd6\xc1'
enc2 = b'p\xfd\x1ff\xcaB\xa5\xe6`\x87\xa8\x8ci\x855\x92O8P\xa5}^\xd8\xed\x1a\x88=c\xe0\x9f\xedq\xf8\xe1%\x7fX\xd2\xba\xbe\x03\xa8\x9a\x9c\x075\x98"\xca\xed\xa4C^\xc6.j\xec\xfa\x10\xa7\xd9\x01\x06\x87\x90f\xcc\xf6\x1b\x0c\xde\xcc,\xfb\xf0\xc74\x94\xcfj\x8ay\xd5\xd2`.@\xed\xc2\xd8!DSp\xf5\x12f\xf1\xf6#\x80\xbe\x16\xa8\xaeF\xd0\xd1\xd4\xad\xb9\xf7#\x16\x08\xb2[\x1a\x87\x8b\xa0\xfaEF\xbf\x86\x8b\x8c\x90\xa4\xd5\xfbcR\xe2W\x9c\n5\x8b\xcfQ"\xf2\x16\x10\xb2I\x1a\x88\x8b\x8cj\x16\xebp\xccS\xd2\x90\xa8|q\x05\xafq\xfa\xcaHE{\x1a\xba#\xfd\x17/\xb2L\x1a\x87\x8a\x90\xc9Dmp\xef\x0ef\xf2Z|S\x00R\xfc\x1c\x9d\n5\x84\xceS\xb0\xa4M_\xff\xb9\x1a\x8a\x1d\\\x98D\\p\xcb*f\xdcV\xd0\xd5Q\xec\x1a\xfa\xf0\x91\xa8\xd4\x8a\xca\x9c-\x17\x07\xb2_\xff\n\x8a\x83\xfb\xc2\x00\x10\x87\x83\xaeF\xf7#\xd4\xbe\'\xa9\x8a$IMp\x14\xe8\xc0\xa4z\xd1\xb2H\xe6e\x8b\xb0\xcf\xb1\x01<\x87\x88g\xc2Q|H\xbe9\xa9\xad\x9c#4\x8cl8I\x0c\x17$\xb3}\x1b\x94\x01:j7\x00;\x86\xbd\xd2i\xf6\x1a\xa4\'R\xf6?\x9c\x08\xe1\xd4\xab\xdd\x8f\xa4[_\xca/@\xed\xe86\xf7\x9c\x018i\x04\xc3\x90\xa8\xaa\x0c\xde\xf2\xa8\xba?\xf4\xd39\xce\\"\xfe\x16\x0cY/]\xed\xe9l\xce\xa5\x018o,g\xdb\xf7\x12\xdag\xb6=\xfa\xccHgk\xcfH\xbf\x18\x9e\xbd\xb3u\x8f\n$Hk\x0e\xd3\xa6i\xe1\x15=\x16}R]\xb3\xa8\x82\x9b\x0b4\x9a\xcf{\xc2\xa4V\xe8:\x93\x1a\x83\x8a\x97j\t\x82\x88\x86\x80f\xf6*\xa2\xd5\xbe\x08\xa9\x98\x9c#\xf8\\\xceV\xa7\xa5L\xae&/t\xec\xfb\xd9\x02Dnp\xe8Cf\xf0U}R4\x87a\xfb\xf0I_\xd4\xaa\xb4"\xca\x16\x18>/i}\t\x03\xc1\x84\x00!\x86\x93g\xed\xf7\x1d\xc3\xbf\x01c\x06KI[\xd5\x929g\xa4t\x87\xb2\\\x1b\x8d\x0b\xd9\x0bDp\xf5om\xe1\x16\x0e}|ZR\xc4\xfb\xf2H@\xd4\xa28\\c\x17&\x07\xc8\xda~\x8b\x88\x86DS\xeb\x87\x87f\xda\xf73\r\xcaS\xd9\xfa\xfaI`\xd5\x889^R\x97\xaeF\xf6\x1a\x92N\xd8*Er\xc3\x16\xe0)\x91\xba|_Q\x83\x00>;\xff5\x82\xceX"\xd7\x17\x08P\xae\x1a\xb1\x8a\x8f\xc9Ep\xa7\x86\x86g\xf6m|o\xbf\x1c\xa9\xa1\x9c+\xc9\x1e\xcfI#\xfc\x92^\xc1\xb8\x1b\xad\x8a\x9e\xceEu\xb8$\xe0\x0b\x90\x87}[\x0fS\xcab]\xd2\xaaU\xcfh"\xfc\xa2_\xdd/y<C\x05k\x18\x00\x1aw\x1e\x9cA\xf6\x0f\x80w\x83\xae\xb8\x9d\x0e\xdc\xd4\xaf9H\\\xaf\x9ey\xef\x1b\xb4.\xd99Dd\xa2\x87\xa7f\xc6\xf6\n\x0c\xc4R\xd7\xfa\xe4Hc\xd4\xa78Jc\x9c^\xca.u\xed\xfcak&\x8b\x92\x87\x88\xee\x90\x83\x90\x0c\xd9R\xcd\x08\x9c04\xb1\xceC"\xea\xe9^\xe3\xd4\x1a\x9a\x0c[\xfa\xc5\x97\xf5>\x15\xc71\x06\x8d\xac\x19\xa0\t\x0el\xe9\xc6%4\x9d\x80U\xe3\xfdF\x8d\xee\x17.+\x9b\xb3\xf0\x83w\x16\xd9'
k4 = [0]*15
k5 = [0]*31
k4[14] = enc1[809]^ord('}')
for i in range(14,810,15):
k5[i%31] = enc2[i]^enc1[i]^k4[14]
for i in range(810):
if chr(enc2[i]^k5[i%31]) in dirct:
print(chr(enc2[i]^k5[i%31]),end='')
else:
print(end='|')简单说下这个的思路。
最后一个字符一定是右大括号。所以k4[14] = enc1[809]^ord('}')。
由于800+个字节,k4,k5分别与明文进行循环异或,k4[14]与k5[i]都有至少一个等式关系的存在。所以可以依次求出k5[i]。完美绕过lfsr。
简单的密码3
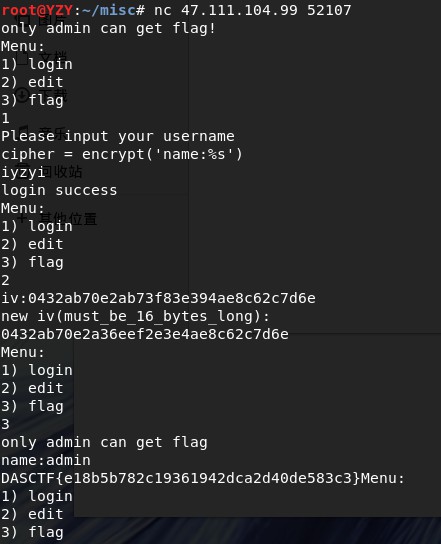
原题没保存,因为这题没给附件,只给了一个ip和端口。
nc上去是一个程序,输入用户名,如果是admin,则可以获取flag。
但是直接输入admin是不被允许的。但是你可以控制iv。由于是黑盒加解密,所以只能猜算法。由于iv可控,我第一反应就是猜测伪造明文攻击,哦呼,三血到手。
def solve(iv, name):
iv_list = []
for i in range(len(iv)//2):
iv_list.append(int(iv[i*2:i*2+2], 16))
for i in range(len(name)):
iv_list[i] ^= ord(name[i]) ^ ord('name:admin'[i])
new_iv = ''
for i in iv_list:
if len(hex(i)[2:]) == 1:
new_iv += '0' + hex(i)[2:]
else:
new_iv += hex(i)[2:]
print(new_iv)
solve('0432ab70e2ab73f83e394ae8c62c7d6e', 'name:iyzyi')