菜死了。。。
吐槽
本场比赛又名:观赏学长虐菜赛,运气局部失灵赛,坐的屁股疼赛,开局死活无法进入比赛环境最终发现没挂学校VPN赛,寄几的本机、虚拟机以及服务器环境全线崩溃赛,倒数第一临危不乱靠半小时加时莽进前十赛,等等。
原来想今晚休息休息的,但是吃鸡时死活没法集中注意力,还是先来写完题解吧。
比赛网址http://219.219.61.234:12345/users,需挂校园VPN。听张老师说国庆期间比赛环境保留。可以回头补一下题。
MISC
两岁半的猪

Stegsolve图片三色素。这张图片以前见过哒。
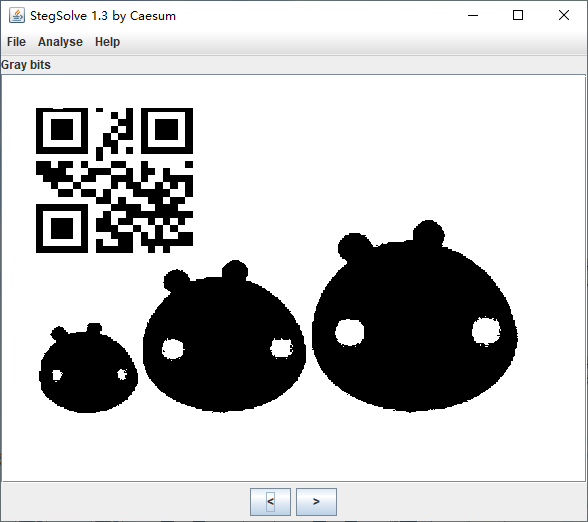
寻找你的Key
伪加密,修改09为00

解压后得到kEy.exe,其实不是exe文件,winhex打开后(局部图)
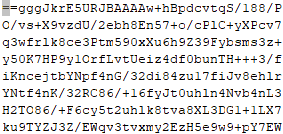
怀疑时base64字符串反序存储。下面的脚本将其再次反序,获得正序的base64字符串
with open(r'd:\桌面\kEy.exe','rb')as f:
b = f.read()
b = b[::-1]
with open(r'd:\桌面\1.png','wb')as f:
f.write(b)正序为(局部图)
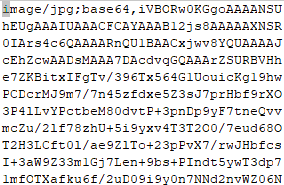
这是把图片数据base64了。可以用python的base64解码。
这里我介绍一个之前写Typecho博客上传工具时了解到的一个知识点。
在Markdown中插入图片,语法标记很简单,用的标记和插入链接很像,只是前面多了一个感叹号。


用Base64编码插入Markdown图片,格式就是在原本写图片地址的()内写上data:image/png;base64,,然后后面跟上base64串

仿照上面的格式,我们将之前的base64字符串写入markdown文件中

兔兔最可爱了
(插入题目图片时出错,Typora(一款markdown编辑器)卡住,排查发现是图片最后形如ke的字符串的锅,删掉这串字符串就可以正常插入了。但是这道题考的就是这串字符串,笑哭,这里就不放题图了)
winhex打开,图片最后

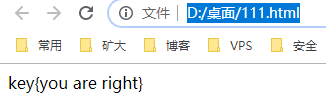
复制到网址栏,回车

原理就浏览器自动将网址栏的字符串转码。
或者可以新建一个网页,写入内容:
ey{you are right}
保存好打开
相关知识:
形如&name; &#dddd; &#xhhhh;的一串字符是 HTML、XML 等 SGML 类语言的转义序列(escape sequence)。它们不是「编码」。以 HTML 为例,这三种转义序列都称作 character reference:第一种是 character entity reference,后接预先定义的 entity 名称,而 entity 声明了自身指代的字符。
后两种是 numeric character reference(NCR),数字取值为目标字符的 Unicode code point;以「&#」开头的后接十进制数字,以「&#x」开头的后接十六进制数字。
逆向
Hook
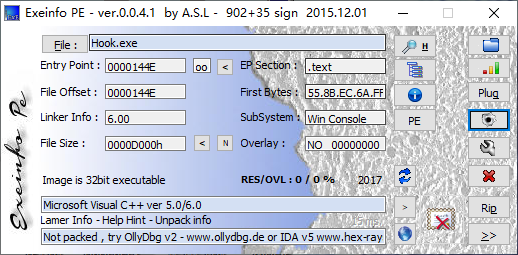
主函数

长度19。跟进sub_401220()
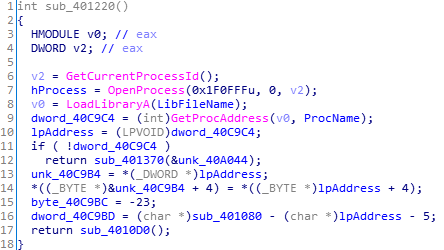
看不懂哎,大概应该是hook,就是劫持句柄,调用API?(存疑)
不过可以去繁就简,跟进sub_401080()。(你问我为什么?我只能说写题解时一句话写起来容易,但是比赛时我是把每个非标准函数(sub开头的)都看了一遍的。可以从函数窗口中把每个sub开头的函数都大体看一下,对算法有个大体的了解)
再根进sub_401000()。
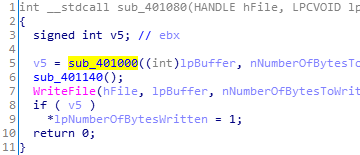
sub_401000()即为加密的关键函数
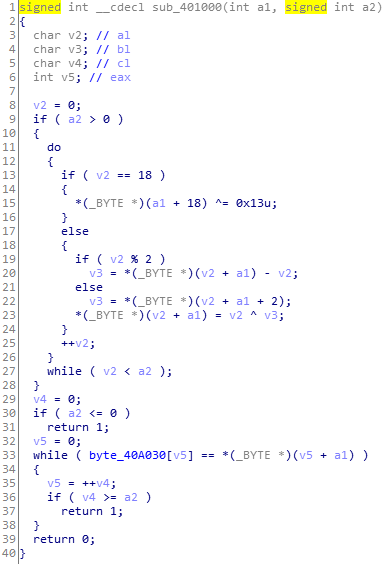
按照实际用途修改变量名如下
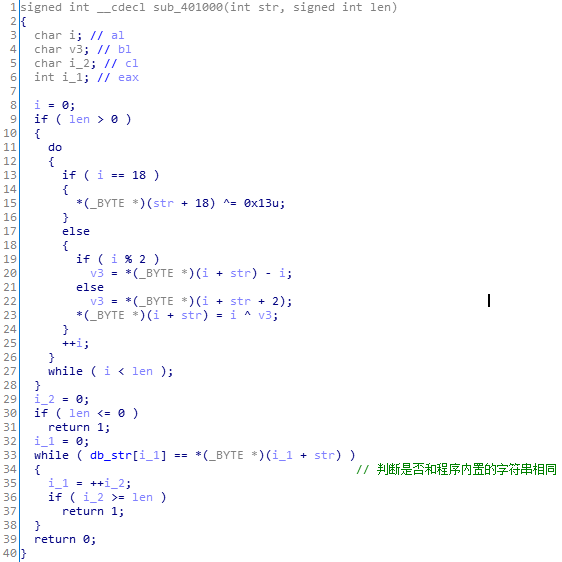
算法为对于传入的字符串a,有以下置换:
char = [0x61,0x6a,0x79,0x67,0x6b,0x46,0x6d,0x2e,0x7f,0x5f,0x7e,0x2d,0x53,0x56,0x7b,0x38,0x6d,0x4c,0x6e]
dict = {}
for i,c in enumerate(char):
if i == 18:
dict[str(i)] = chr(c ^ 19)
elif i % 2:
dict[str(i)] = chr((c ^ i) + i)
else:
dict[str(i+2)] = chr(c ^ i);
for i in range(20):
try:
print(dict[str(i)],end='')
except:
pass代码中使用了字典,key为0~18。
输出为lag{Ho0k_w1th_Fun}
emmm,一猜就知道前面少了个f,就是不知道哪里出了问题。估计是数据少抄了一个。
补充
刚刚读了FX-Ti大佬的题解,对Hook有了更深的理解。
具体可去他的博客看。这里我就不复制啦
算了还是摘抄关键部分吧。
首先查看main函数:
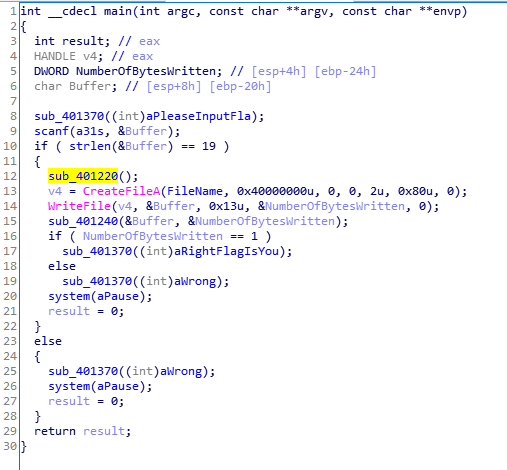
正常的读去用户输入然后限定长度是19个字符,再走过黄标的函数之后经过sub_401240函数的检验。
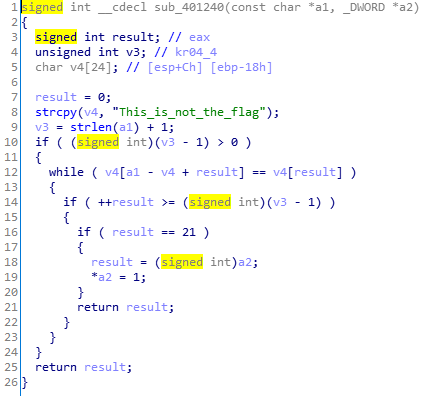
函数中的”fake flag”字样表明这并不是真正的检查函数,于是仔细看下之前的黄标函数。
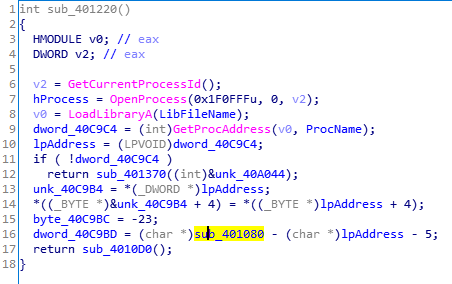
里面开启内存的可写权限然后替换WriteFile函数为图中的黄标函数,进入黄标函数就可以看到真正的检查函数sub_401000。
Cracker
hint: 就解方程
这个题看的时间贼长。OD和IDA统统上阵。当然也是靠这道题从并列倒数第一冲到第八。(主要是除了前三的学长,大家基本都只有一道题的分数差距)
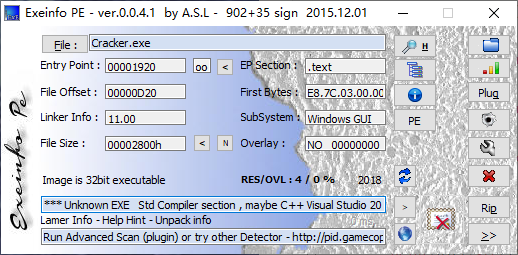
直接打开时提示缺少MSVCR110.dll,按照https://helpx.adobe.com/cn/creative-cloud/kb/error-opening-applications-in-windows-10.html 的提示,
来到 https://www.microsoft.com/zh-cn/download/details.aspx?id=30679,
我先尝试了x64的,但是还是不行,于是尝试下载并安装x86.exe,此时可以了。估计是程序是32位的缘故。
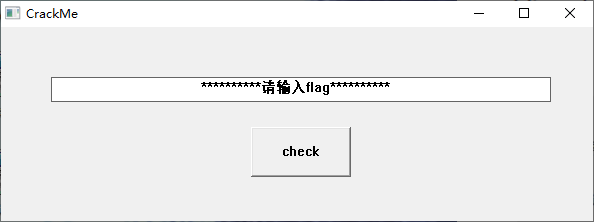
看的时间长了,初步确定程序运行路线为:
WinMain中调用sub_4013E0.
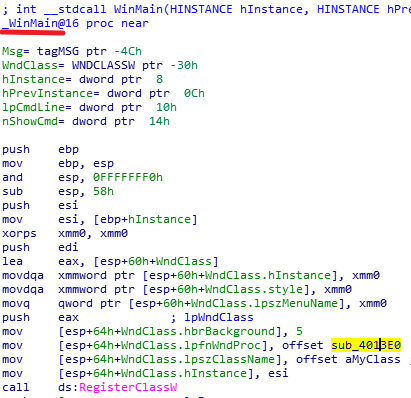
sub_4013E0为输出成功或失败的函数(下图),6666时成功。我们跟踪其中的sub_401350
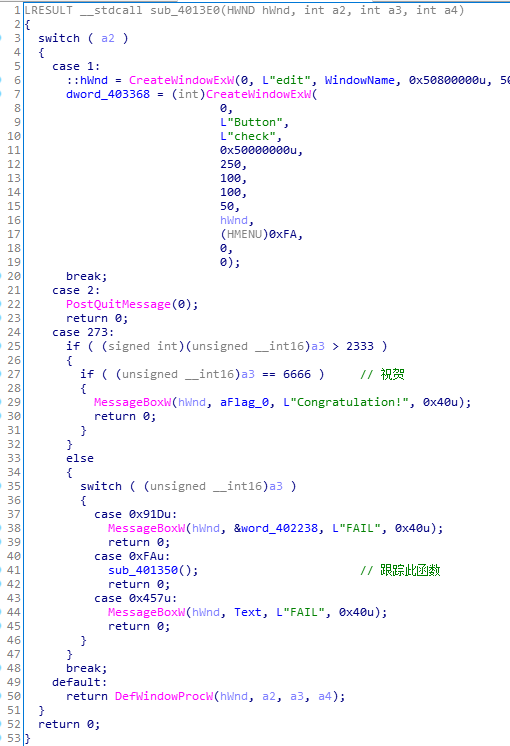
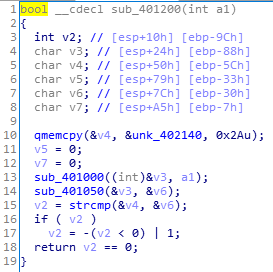
sub_401350(下图)中获取了输入的字符串&string。跟踪if则发送6666文本中的条件:sub_401200
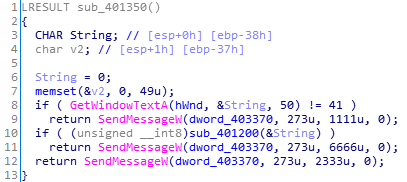
sub_401200(下图)发现了一个函数sub_401000,以及第14行的未知操作。unk_402140为内置字符串(显示为汉字,反正没有英文)
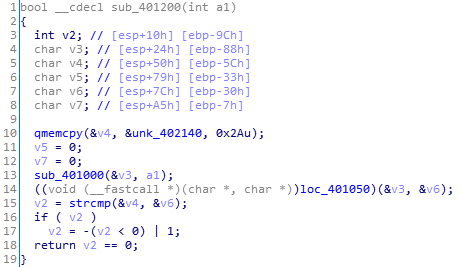
跟进其中的sub_401000(下图)。算法就是置换a2中的字符相对位置,然后赋值给a1。
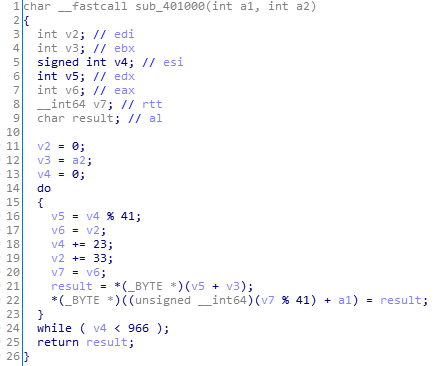
跟进14行的loc_401050,有下图:
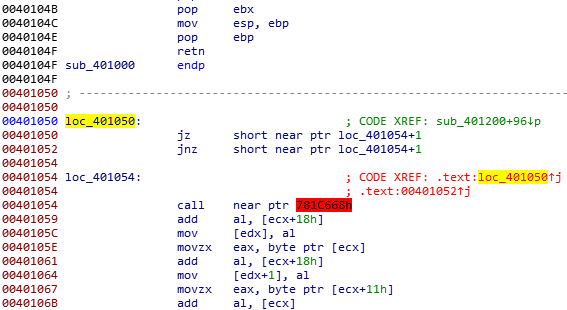
你会发现0x401050和0x401052处的跳转都是跳转至0x401054+1,而不是红色背景那一行的0x401054.
但是0x401054这一行的命令跳转至了一个不存在的位置,ida分析不出来,因为后面的操作无法分析出一个函数。
把这行命令nop掉就好了。
操作如下图:
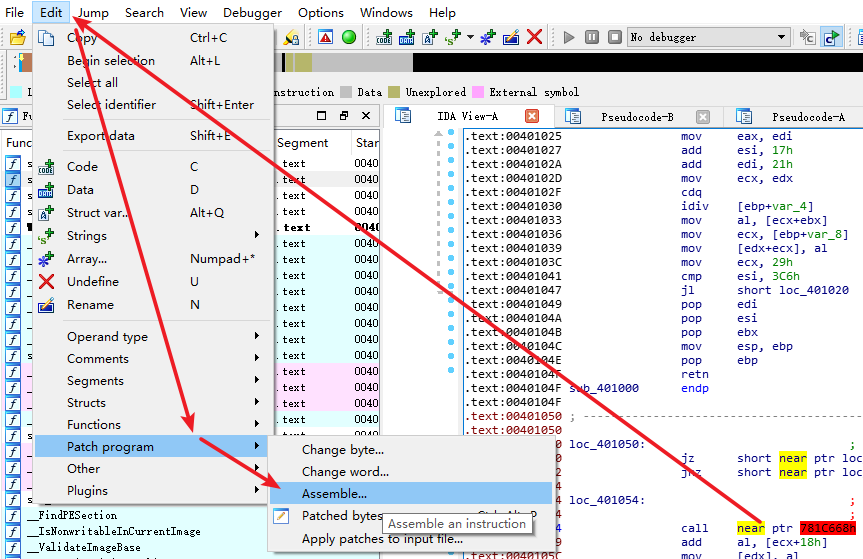
文本框中改为nop,点击OK。
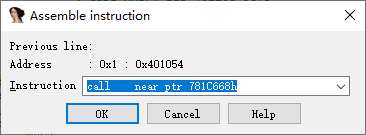
除了上面的那处,还有下面的这处,同样nop掉
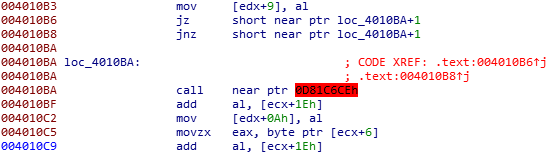
接着如下图操作:
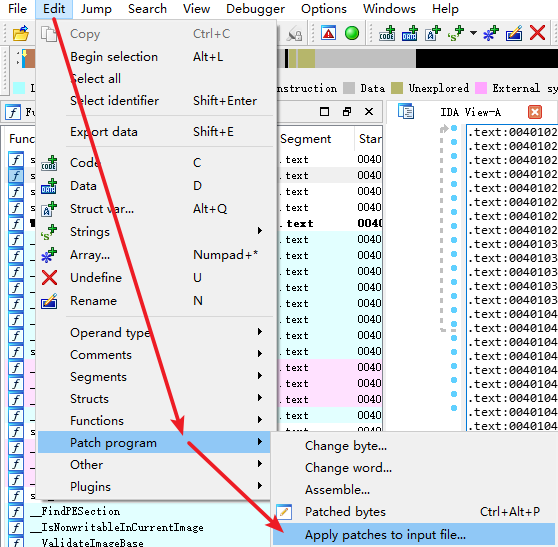
然后重新用ida加载程序,你会发现sub_401200中的未知操作分析成函数sub_401050了。
跟进sub_401050,提示中的方程组出来了
回到sub_401200(下图)
分析整体流程为:
v4为程序内置已知字符串,a1为输入字符串(由sub_401350可知)。
将a1进行置换,结果保存在&v3
v6[i] = v3[j] + v3[k]类型的方程组
比较v4和v6是否相同
然后判断。
反过来解密的思路为:
由已知v6(因为v4=v6),解方程组求v3
然后置换求a1
解方程组应该可以用python,但是时间紧急,环境我没有配置好,就找了个在线解方程组。
http://www.yunsuan.info/matrixcomputations/solvelinearsystems.html
解方程组肯定需要把数据给出呀,所以写了个正则。
将方程组保存至1.txt,如下:
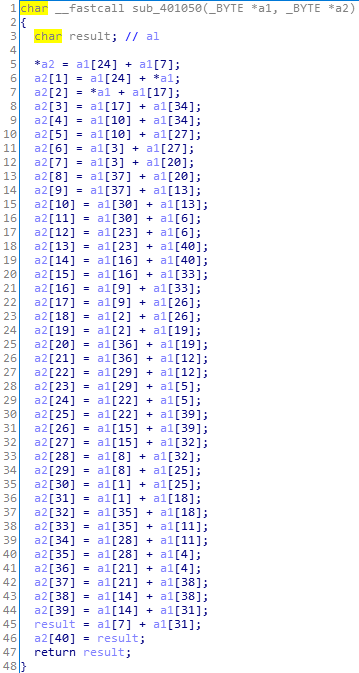
a2[0] = a1[24] + a1[7];
a2[1] = a1[24] + a1[0];
a2[2] = a1[0] + a1[17];
a2[3] = a1[17] + a1[34];
a2[4] = a1[10] + a1[34];
a2[5] = a1[10] + a1[27];
a2[6] = a1[3] + a1[27];
a2[7] = a1[3] + a1[20];
a2[8] = a1[37] + a1[20];
a2[9] = a1[37] + a1[13];
a2[10] = a1[30] + a1[13];
a2[11] = a1[30] + a1[6];
a2[12] = a1[23] + a1[6];
a2[13] = a1[23] + a1[40];
a2[14] = a1[16] + a1[40];
a2[15] = a1[16] + a1[33];
a2[16] = a1[9] + a1[33];
a2[17] = a1[9] + a1[26];
a2[18] = a1[2] + a1[26];
a2[19] = a1[2] + a1[19];
a2[20] = a1[36] + a1[19];
a2[21] = a1[36] + a1[12];
a2[22] = a1[29] + a1[12];
a2[23] = a1[29] + a1[5];
a2[24] = a1[22] + a1[5];
a2[25] = a1[22] + a1[39];
a2[26] = a1[15] + a1[39];
a2[27] = a1[15] + a1[32];
a2[28] = a1[8] + a1[32];
a2[29] = a1[8] + a1[25];
a2[30] = a1[1] + a1[25];
a2[31] = a1[1] + a1[18];
a2[32] = a1[35] + a1[18];
a2[33] = a1[35] + a1[11];
a2[34] = a1[28] + a1[11];
a2[35] = a1[28] + a1[4];
a2[36] = a1[21] + a1[4];
a2[37] = a1[21] + a1[38];
a2[38] = a1[14] + a1[38];
a2[39] = a1[14] + a1[31];
a2[40] = a1[7] + a1[31];python正则脚本:
import re
with open (r'1.txt', 'r')as f:
s = f.readlines();
for i in s:
r = re.search(r'a2\[(\d+)\] \= a1\[(\d+)\] \+ a1\[(\d+)\];', i)
n = [0] * 41
n[int(r.group(2))] = 1
n[int(r.group(3))] = 1
print(str(n)[1:-1])输出为
0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0
0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0上面的数据,一行是一个方程式的41个未知数的系数,填入系数矩阵
然后从程序中提取内置的那个已知的字符串,写个逐行输出的python脚本
db = [0x97, 0xB1, 0xC8, 0xCD, 0xD5, 0xD2, 0x96, 0x94, 0xB8, 0xB4, 0xC5, 0xDA, 0xA4, 0x71, 0x71, 0x8F, 0xBE, 0x94, 0xA4, 0xD0, 0xDE, 0xF3, 0xD5, 0xD4, 0xD4, 0xC4, 0xD9, 0xE5, 0xC1, 0xC4, 0xD5, 0xDA, 0xF4, 0xE7, 0xC1, 0xBE, 0xD7, 0xC1, 0x96, 0x64, 0x6A]
for i in db:
print(i)输出的字符串填入右边向量。
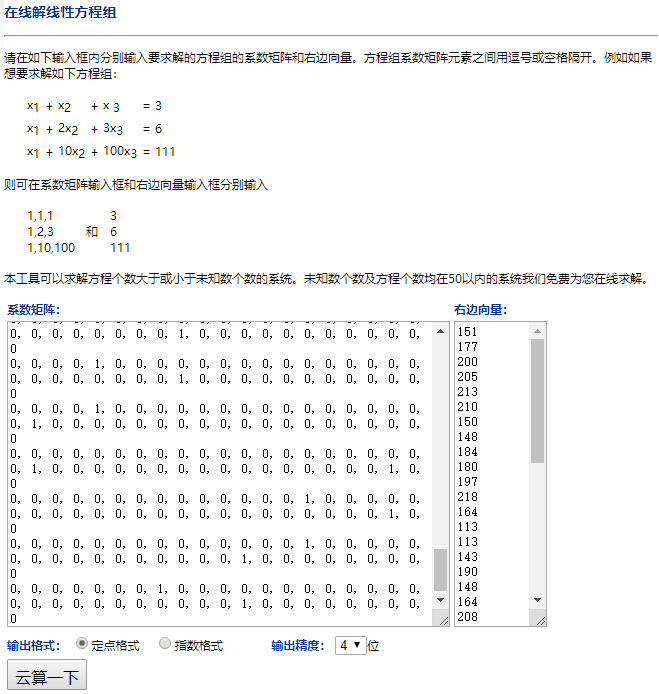
得到结果
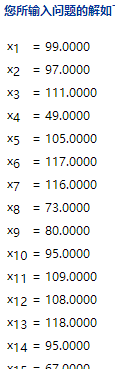
注意,计算结果页面开头是输出的是系数矩阵和右边向量。我开始时看到输出一堆零,以为哪里算错了。其实没有,使劲向下翻,就可以看到结果了。
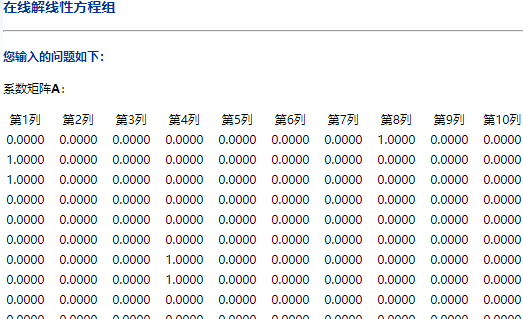
将结果写入python脚本,并模拟置换
a1 = [99,97,111,49,105,117,116,73,80,95,109,108,118,95,67,116,48,101,121,97,99,110,95,48,78,116,53,101,85,95,102,33,113,95,104,123,125,85,83,101,65]
a2 = [0] * 41
v2 = 0
v4 = 0
for i in range(966//23-1):
v5 = v4 % 41
v6 = v2
v4 += 23
v2 += 33
v7 = v6
a2[v5] = a1[v7 % 41]
for i in a2:
print(chr(i),end='')输出cumtctf{Ai_CaN_he1P_y0U_SoIve_eqUatl0n5!}
这道题虽然麻烦,但是在最终时刻保住了我作为菜鸟的尊严啊。
z3解方程组
读了FX-Ti大佬的题解后,才知道z3也可以解方程组,参考了他的python脚本,写出我的,和他的有些区别(疯狂暗示不是直接复制粘贴哒)。
FX-Ti大佬牛逼(破声)
from z3 import *
import re
set = '''
a2[0] = a1[24] + a1[7];
a2[1] = a1[24] + a1[0];
a2[2] = a1[0] + a1[17];
a2[3] = a1[17] + a1[34];
a2[4] = a1[10] + a1[34];
a2[5] = a1[10] + a1[27];
a2[6] = a1[3] + a1[27];
a2[7] = a1[3] + a1[20];
a2[8] = a1[37] + a1[20];
a2[9] = a1[37] + a1[13];
a2[10] = a1[30] + a1[13];
a2[11] = a1[30] + a1[6];
a2[12] = a1[23] + a1[6];
a2[13] = a1[23] + a1[40];
a2[14] = a1[16] + a1[40];
a2[15] = a1[16] + a1[33];
a2[16] = a1[9] + a1[33];
a2[17] = a1[9] + a1[26];
a2[18] = a1[2] + a1[26];
a2[19] = a1[2] + a1[19];
a2[20] = a1[36] + a1[19];
a2[21] = a1[36] + a1[12];
a2[22] = a1[29] + a1[12];
a2[23] = a1[29] + a1[5];
a2[24] = a1[22] + a1[5];
a2[25] = a1[22] + a1[39];
a2[26] = a1[15] + a1[39];
a2[27] = a1[15] + a1[32];
a2[28] = a1[8] + a1[32];
a2[29] = a1[8] + a1[25];
a2[30] = a1[1] + a1[25];
a2[31] = a1[1] + a1[18];
a2[32] = a1[35] + a1[18];
a2[33] = a1[35] + a1[11];
a2[34] = a1[28] + a1[11];
a2[35] = a1[28] + a1[4];
a2[36] = a1[21] + a1[4];
a2[37] = a1[21] + a1[38];
a2[38] = a1[14] + a1[38];
a2[39] = a1[14] + a1[31];
a2[40] = a1[7] + a1[31];
'''
a2 = [0x97, 0xB1, 0xC8, 0xCD, 0xD5, 0xD2, 0x96, 0x94, 0xB8, 0xB4, 0xC5, 0xDA, 0xA4, 0x71, 0x71, 0x8F, 0xBE, 0x94, 0xA4, 0xD0, 0xDE, 0xF3, 0xD5, 0xD4, 0xD4, 0xC4, 0xD9, 0xE5, 0xC1, 0xC4, 0xD5, 0xDA, 0xF4, 0xE7, 0xC1, 0xBE, 0xD7, 0xC1, 0x96, 0x64, 0x6A]
s = Solver()
a1 = []
for i in range(41):
a1.append(BitVec('a1_'+str(i), 8)) #8位BitVec变量
lines = set.split('\n')[1:-1] #第一个和最后一个元素为空
for i in lines:
r = re.search(r'a2\[(\d+)\] \= a1\[(\d+)\] \+ a1\[(\d+)\];', i)
s.add(a2[int(r.group(1))] == a1[int(r.group(2))] + a1[int(r.group(3))]) #等式是两个等号哦
print(s.check())
for i,name in enumerate(a1): #a1=[a1_0, a1_1, a1_2, a1_3, a1_4,...]
#print('{}: {}'.format(i, s.model()[i].as_long()))
a1[i] = s.model()[name].as_long() #现在a1为[99, 97, 111, 49, 105,...]
#模拟置换,这里的a2和前面的a2不是一个哦
v2 = 0
v4 = 0
for i in range(966//23-1):
v5 = v4 % 41
v6 = v2
v4 += 23
v2 += 33
v7 = v6
a2[v5] = a1[v7 % 41]
print("".join(list(map(chr, a2))))matlab求解
本部分为2020.7.26补充
前面说的那个在线求解其实应该使用matlab求解的。
今天一个国际赛的逆向题也是求解方程组,当然不完全是,要考虑溢出。虽然这道题我没做出来,但是借此学习了一下matlab求解方程。
过程如下:
>> A = [2,3,1;
4,2,3;
7,1,-1];
>> B = [4;17;1];
>> X = A\B
X =
1.0000
-1.0000
5.0000
>> C = [0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0;
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0;
0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0];
>> D = [151;177;200;205;213;210;150;148;184;180;197;218;164;113;113;143;190;148;164;208;222;243;213;212;212;196;217;229;193;196;213;218;244;231;193;190;215;193;150;100;106];
>> X = C\D
X =
99
97
111
49
105
117
116
73
80
95
109
108
118
95
67
116
48
101
121
97
99
110
95
48
78
116
53
101
85
95
102
33
113
95
104
123
125
85
83
101
65
>> 数据chr一下就是flag
写在后面
国庆再补题吧,明天要复习一下电工、大物和高数了,这学期基本没听过课。主要是快考试了,怕挂科。(第三天晚上补充:其实昨天水了一天。。。)
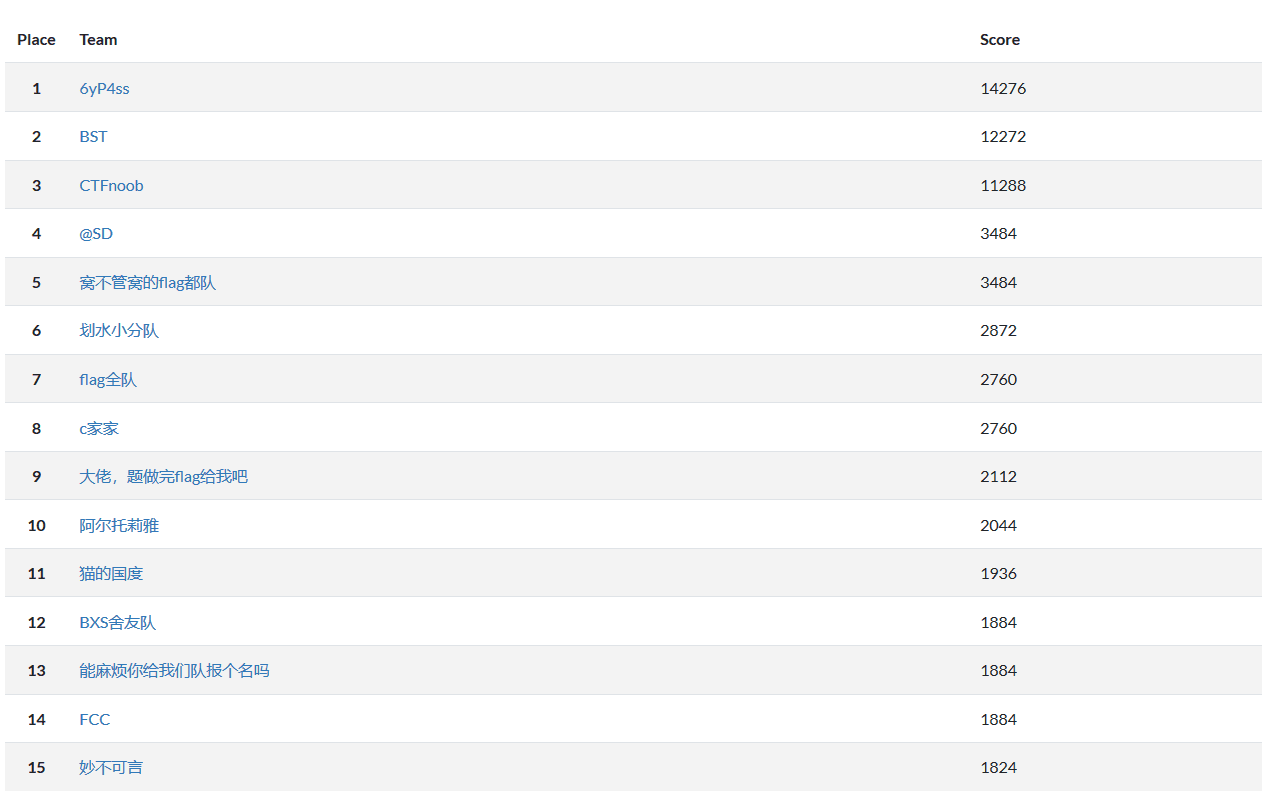
最后放上最终成绩,队名c家家
强,我懒得给我的博客添加评论功能OωO
你博客真好看
你也很强呀|´・ω・)ノ
misc比我好 ,强